> About Author
Hi, I'm Sharon, a product manager at Chaitin Tech. We build SafeLine, an open-source Web Application Firewall built for real-world threats. While SafeLine focuses on HTTP-layer protection, our emergency response center monitors and responds to RCE and authentication vulnerabilities across the stack to help developers stay safe.
Apache OFBiz, the open-source ERP framework used by many enterprises, was recently found vulnerable to a critical Remote Code Execution (RCE) flaw — tracked as CVE-2023-49070. This vulnerability allows unauthenticated attackers to execute arbitrary code on the server, making it a high-impact issue for businesses relying on OFBiz.
TL;DR
- CVE ID: CVE-2023-49070
- Impact: Remote Code Execution (no auth required)
- Affected versions: All versions prior to 18.12.10
- Fix: Upgrade to 18.12.10
- Detection supported by: SafeLine WAF, Yuntu, Quanshi
Vulnerability Background
This vulnerability stems from a long history of partial fixes:
- 2020: Authentication checks were added to patch CVE-2020-9496 — but bypasses remained.
- 2021: Filters were introduced to block malicious XML-RPC calls — again, bypassable.
- 2023 (April): Developers finally removed the XML-RPC handler in the main branch. However, only version 18.12.10 officially removes the XML-RPC feature in release builds.
Older releases still expose the vulnerable XML-RPC interface.
Exploitation Characteristics
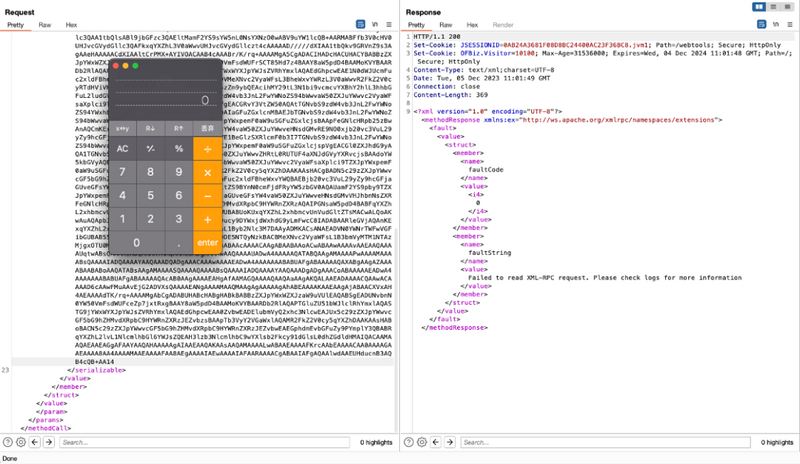
Attackers can abuse the /webtools/control/xmlrpc endpoint with crafted HTTP requests that often include credentials and malicious payloads. Key indicators include:
- Unusual URI patterns (e.g., path traversal using
../or semicolons) - Traffic spikes targeting the
xmlrpcendpoint - Error logs related to XML-RPC deserialization
Impact
This vulnerability poses a serious threat:
- Code Execution: Full server compromise is possible.
- Data Breach: Potential for data theft, manipulation, or exposure.
- Business Disruption: Since OFBiz handles ERP operations, attackers could halt core business workflows.
Mitigation and Fix
Official Fix
Upgrade immediately to the latest version:
🔗 https://ofbiz.apache.org/download.html
Only 18.12.10 fully removes the XML-RPC handler.
Temporary Workarounds
If you can't upgrade right away:
-
Disable XML-RPC: Block or redirect
/control/xmlrpcif it’s not required. - Network ACLs: Restrict external access to the endpoint via firewall rules.
- Monitoring & Logging: Deploy IDS/IPS or WAF (e.g., SafeLine) to watch for suspicious XML-RPC activity.
Reproduction Details
Product Detection Support
| Product | Support for CVE-2023-49070 |
|---|---|
| SafeLine WAF | ✅ Detects exploitation via updated rules |
| Yuntu | ✅ Fingerprint detection and PoC validation |
| Quanxi | ✅ Detects malicious behavior automatically |
Timeline
- Dec 4, 2023 – Vulnerability publicly disclosed online
- Dec 5, 2023 – Chaitin Lab successfully reproduced the exploit
- Dec 5, 2023 – Advisory published by Chaitin Emergency Response Team
References
Stay safe — and if you're using OFBiz in production, patch it now.
Join the SafeLine Community
If you continue to experience issues, feel free to contact SafeLine support for further assistance.



Top comments (0)