If you’re running SafeLine WAF to secure your homelab, internal apps, or self-hosted services, you might not need Cloudflare’s proxy traffic. In some cases, you may even want to block all Cloudflare-originated IPs to keep your network clean and reduce unnecessary requests. SafeLine makes this straightforward with its flexible rule system.
Why Block Cloudflare IPs?
- Restrict access to trusted networks only
- Reduce exposure to automated scanners or unwanted proxy traffic
- Keep internal resources private and off public CDN routes
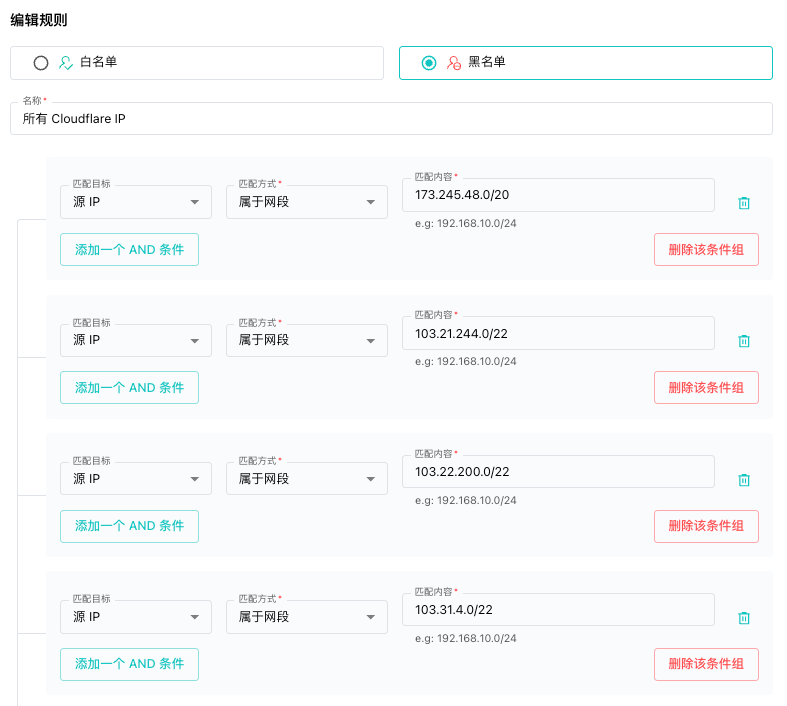
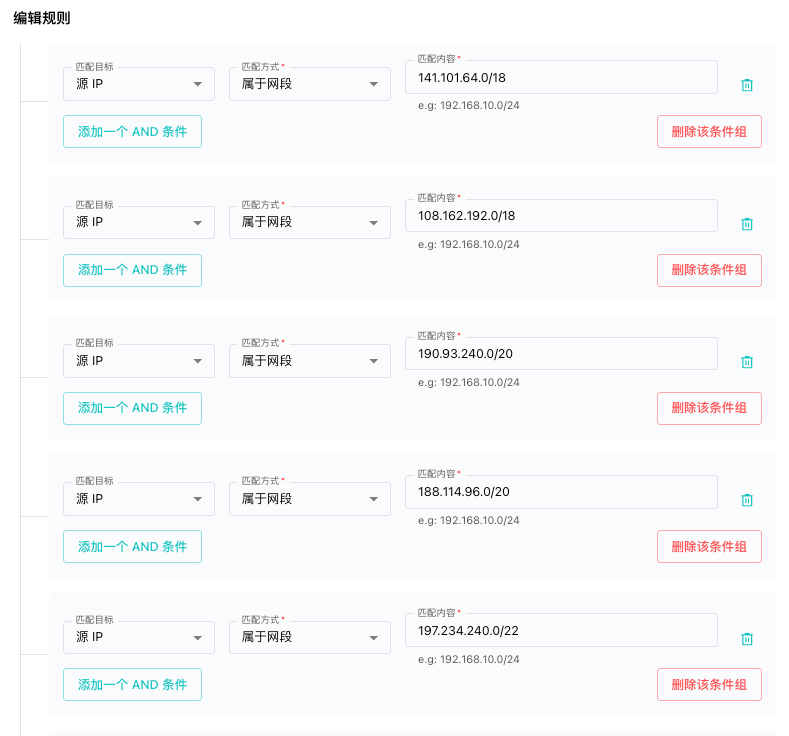
SafeLine WAF Rule Example
Rule library snapshot:
- Whitelist rules: 0
- Blacklist rules: 1
- Supported version: SafeLine 7.3.0 and above
Rule details:
- Type: Blacklist
- Condition: Block any request from Cloudflare’s published IP ranges
Cloudflare maintains an up-to-date list of their IP ranges. To configure your rule effectively, you must reference their official source:
https://www.cloudflare.com/ips/
How to Implement in SafeLine
- Open the SafeLine WAF dashboard.
- Create a deny rule.
- Add Cloudflare’s IPv4 and IPv6 ranges to the blocklist conditions.
- Save and apply the rule to your site or homelab environment.
- Review Cloudflare’s IP updates periodically to keep your blocklist current.
Join the SafeLine Community
If you continue to experience issues, feel free to contact SafeLine support for further assistance.



Top comments (0)