> About Author
Hi, I'm Sharon, a product manager at Chaitin Tech. We build SafeLine, an open-source Web Application Firewall built for real-world threats. While SafeLine focuses on HTTP-layer protection, our emergency response center monitors and responds to RCE and authentication vulnerabilities across the stack to help developers stay safe.
On January 14, 2025, Fortinet confirmed a critical authentication bypass vulnerability affecting its widely-used security products: FortiOS and FortiProxy. Tracked as CVE-2024-55591, the flaw allows unauthenticated remote attackers to gain administrative control over FortiGate firewalls and proxy devices — without needing valid credentials.
The vulnerability has already been exploited in the wild, making it essential to patch immediately if you're using an affected version.
What’s Affected?
According to Fortinet’s advisory, the following versions are vulnerable:
Affected Versions
- FortiGate (FortiOS): 7.0.0 – 7.0.16
-
FortiProxy:
- 7.2.0 – 7.2.12
- 7.0.0 – 7.0.19
Patched Versions
- FortiOS: 7.0.17 and above
- FortiProxy: 7.2.13 / 7.0.20 and above
Upgrade to these versions ASAP to eliminate the risk.
Vulnerability Overview
This flaw stems from improper validation in the authentication logic of FortiOS and FortiProxy. By crafting specific requests to the management interface (HTTPS or CLI Web Console), attackers can completely bypass authentication, gaining super admin privileges remotely.
Once inside, attackers can:
- Create or reset admin accounts
- Modify firewall policies
- Configure SSL VPN for lateral movement
- Steal sensitive configurations
- Disable protections or plant backdoors
This is a pre-auth remote vulnerability, meaning no login or prior access is required — default setups are vulnerable.
Recommended Actions
1. Block Public Access to Management Interfaces
Immediately restrict HTTPS, SSH, and CLI access to trusted internal networks only. Use firewalls or ACLs to allow specific IPs.
2. Monitor Logs for Suspicious Logins
Look for unusual login activity from IPs like 127.0.0.1 or 8.8.8.8, especially using the jsconsole UI or strange admin usernames.
3. Check for Backdoors or Tampering
Export current device configurations and verify them for unauthorized changes or files. If compromise is suspected, involve Fortinet support or a trusted security team.
4. Reset All Admin and VPN Credentials
If compromise is likely, rotate all administrator and VPN passwords, revoke old certificates, and refresh API keys.
Patch and Recovery
Apply Official Fixes
Fortinet has released patches for all affected versions. Update immediately via FortiManager, or refer to:
Full Reinstall if Breached
If you have strong evidence of compromise, Fortinet recommends:
- Performing a factory reset
- Reinstalling the firmware from clean images
- Importing safe configurations
- Re-validating integrity with checksum tools
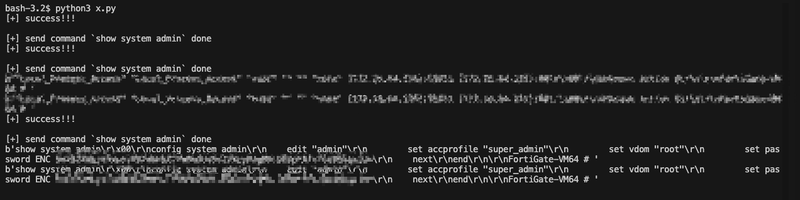
Reproduction
Real-World Exploitation Confirmed
- Jan 15, 2025: Public disclosure and active in-the-wild exploitation reported
- Jan 16, 2025: Exploit confirmed and reproduced by security researchers
This vulnerability — nicknamed “Console Chaos” by some researchers — is being actively weaponized. Immediate action is critical for all FortiGate and FortiProxy administrators.
References
- Fortinet PSIRT Advisory: FG-IR-24-535
- Arctic Wolf Research: Console Chaos Targets FortiGate
Join the SafeLine Community
Want to try a powerful, open source WAF?
Stay alert. Patch fast. Monitor always.



Top comments (0)