> About Author
Hi, I'm Sharon, a product manager at Chaitin Tech. We build SafeLine, an open-source Web Application Firewall built for real-world threats. While SafeLine focuses on HTTP-layer protection, our emergency response center monitors and responds to RCE and authentication vulnerabilities across the stack to help developers stay safe.
Smartbi is a widely used enterprise Business Intelligence (BI) platform that provides data visualization, multi-source integration, and reporting features. It’s designed to help organizations analyze data efficiently and make smarter, data-driven decisions.
On July 31, 2025, Smartbi released a security patch fixing a Remote Code Execution (RCE) vulnerability. This flaw allows attackers to bypass authentication and trigger dangerous backend methods, ultimately achieving remote command execution on the affected server.
The exploit difficulty is low, and the potential impact is critical — making this a high-priority patch for all Smartbi users.
Vulnerability Overview
Root Cause
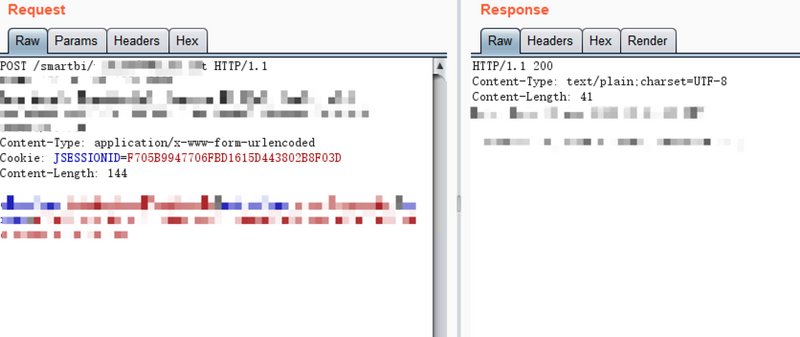
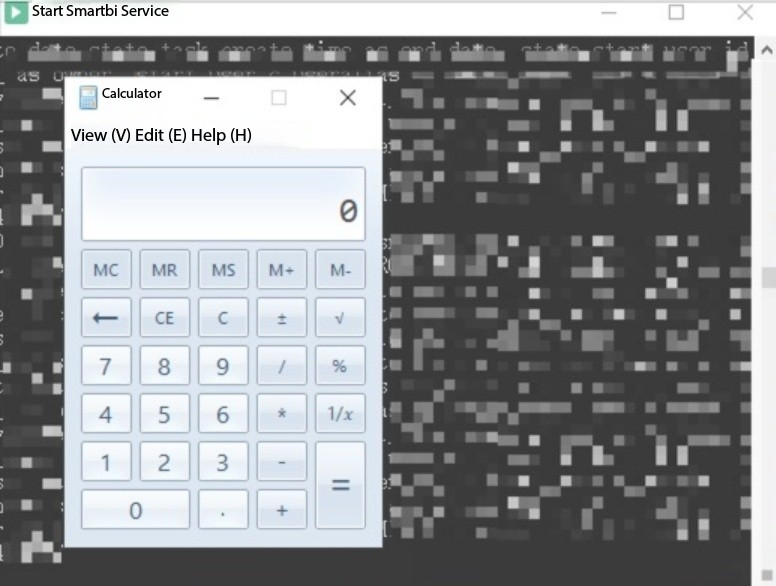
The authentication mechanism in Smartbi contains a design flaw. Attackers can leverage a default resource ID to bypass session validation and obtain valid session tokens. With this, they can invoke backend APIs to reflectively call dangerous methods, resulting in remote code execution.
Impact
- Full server takeover
- Data exfiltration
- Compromise of business-critical systems
Vulnerability Details
- Type: Remote Code Execution (RCE)
- Severity: High
- Attack Vector: Remote (network-based)
- Auth Required: None
- User Interaction: None
- System Requirements: Default configuration
- Exploit Availability: No public PoC/EXP yet
- Fix Complexity: Low (official patch available)
Affected Versions
- Smartbi <= 11.0.99471.25193
Solutions
Permanent Fix
Upgrade to the latest patched version immediately:
👉 Smartbi Patch Download
Temporary Mitigation
- Avoid exposing Smartbi directly to the internet if possible.
Proof of Concept (Reproduction)
Product Support
- Yuntu: Supports fingerprinting + PoC detection
- Dongjian: PoC detection support expected on Aug 18, 2025
- SafeLine WAF: Already supports detection of this vulnerability
- Quanxi: Rule update package expected Aug 18, 2025
Timeline
- Jul 31, 2025 — Smartbi releases official security patch
- Aug 18, 2025 — Chaitin Emergency Response Center issues advisory
Join the SafeLine Community
If you continue to experience issues, feel free to contact SafeLine support for further assistance.



Top comments (0)