When you're running any public-facing service—even in a homelab—you may eventually run into hostile traffic, including potential DDoS (Distributed Denial-of-Service) attempts. One simple but effective first step is blocking known malicious IP addresses.
This SafeLine WAF rule library focuses on blacklisting IPs that were flagged for repeated suspicious traffic. It’s perfect for self-hosters, hobbyists, or small teams looking to keep unwanted requests off their network.
Why Block IPs?
- Immediate mitigation: Stops repeat offenders before they consume resources.
- Early defense layer: Useful before implementing more advanced DDoS mitigation.
- Good for small deployments: Lightweight rule set, easy to maintain for homelabs or self-hosted apps.
The Rule in SafeLine
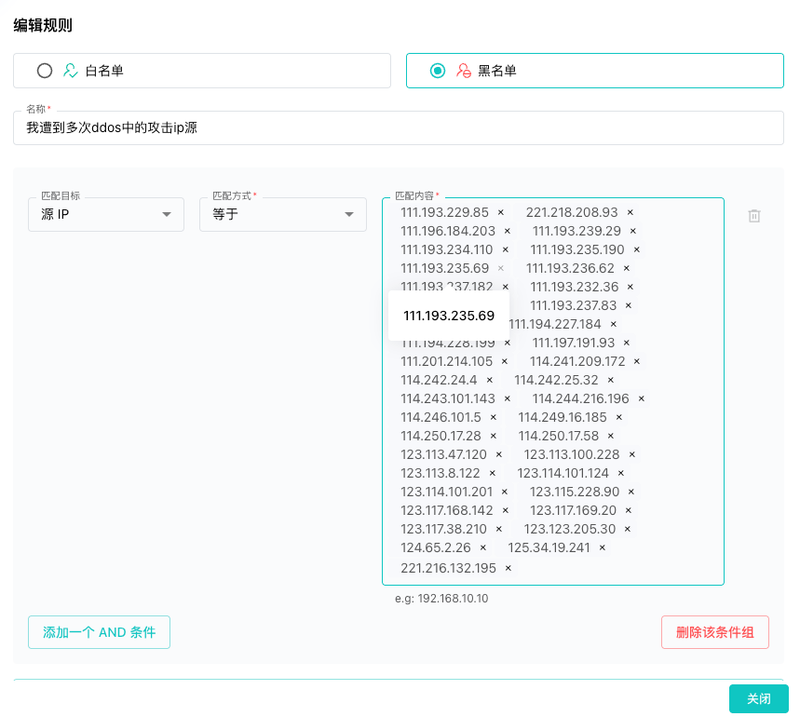
Rule library name: Suspected DDoS IP addresses
Applies to: SafeLine v7.3.0 and above
Lists:
- Whitelist: None
- Blacklist: 1
Blacklist Rule:
- Name: DDoS source IPs
- Match type: Source IP equals
- Example IPs (truncated):
111.193.229.85
221.218.208.93
111.196.184.203
...
125.34.19.241
221.216.132.195
(Use the full list in your SafeLine console.)
How to Set It Up
- Open your SafeLine WAF management console.
- Create a new IP-based rule under your target policy.
- Add the listed IPs to the blocklist (source IP equals).
- Save and deploy.
Important Notes
- Keep it updated: Threat IPs change constantly. Update your blocklist regularly.
- Combine with other measures: IP blocking alone won’t stop a large-scale DDoS. Consider rate limiting, geo-blocking, and upstream protections.
- Test before deploying: Especially important if you’re unsure about false positives.
Join the SafeLine Community
If you continue to experience issues, feel free to contact SafeLine support for further assistance.



Top comments (0)