> About Author
Hi, I'm Sharon, a product manager at Chaitin Tech. We build SafeLine, an open-source Web Application Firewall built for real-world threats. While SafeLine focuses on HTTP-layer protection, our emergency response center monitors and responds to RCE and authentication vulnerabilities across the stack to help developers stay safe.
Apache Struts2, a widely used Java web application framework, has once again come under the spotlight with a new vulnerability — CVE-2023-50164 (also known as S2-066). The issue, disclosed in December 2023, affects Struts versions 2.0.0 to 2.5.32 and 6.0.0 to 6.3.0.1, allowing attackers to potentially upload files to unintended locations on the server and execute arbitrary code.
Vulnerability Overview
The root cause lies in case-insensitive parameter handling combined with insufficient validation of uploaded file paths. Attackers can exploit this to perform directory traversal (../) during file uploads — bypassing access restrictions and uploading files to sensitive locations.
Exploitation Characteristics
- Abnormal Parameter Casing: Exploit requests often use unusual casing for parameters involved in file uploads to trigger unexpected behavior in Struts’s parameter processing.
-
Path Traversal Payloads: Exploit traffic typically includes sequences like
../../../../in file paths to escape the intended directory and target restricted locations.
Potential Impact
If successfully exploited, this vulnerability may lead to:
- Remote Code Execution (RCE): Uploaded scripts or binaries can be executed, giving full control of the host server.
- Data Exposure: Unauthorized file access may expose sensitive configuration files or application secrets.
- Ransomware Deployment: Attackers could upload ransomware payloads to encrypt and hold critical assets hostage.
Affected Versions
- Apache Struts 2.0.0 – 2.5.32
- Apache Struts 6.0.0 – 6.3.0.1
Mitigation & Fixes
Temporary Workarounds
- Input Validation: Sanitize file paths in upload-related handlers. Avoid using user-provided filenames directly in file paths.
- Filename Randomization: Always store uploaded files using randomized or hashed names to prevent predictable access paths.
- Access Controls: Restrict access to vulnerable endpoints via network ACLs or IP whitelisting.
- Logging & Monitoring: Set up alerts for suspicious upload attempts or abnormal path traversal activity.
Official Patch
The Apache team has released a patched version. Upgrade immediately by visiting:
👉 https://struts.apache.org/download.cgi#struts-ga
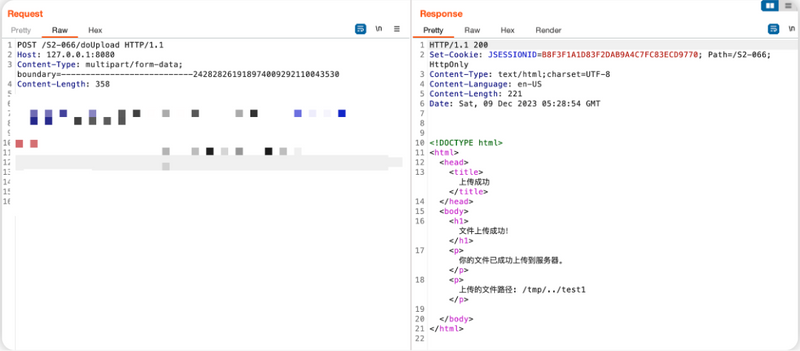
Reproduction
While exploitability depends on specific deployment environments, security researchers have confirmed that the vulnerability is reproducible under certain configurations. Below is a snapshot of a test environment under exploitation:
Detection Tools
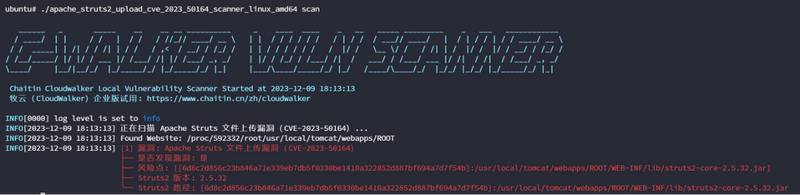
Local Scanner (Muyun)
Use the following tool provided by Chaitin Tech to scan for CVE-2023-50164 locally:
sudo ./apache_struts2_upload_cve_2023_50164_scanner_linux_amd64 scan
Download the tool from:
👉 https://stack.chaitin.com/tool/detail/1262
Vendor Response & Support
- SafeLine WAF: Already supports detection of this exploit pattern out of the box.
- Quanxi: Rule pack released for detection.
- Muyun: Provides vulnerability scanning capability for this CVE.
Timeline
- Dec 7, 2023: Vulnerability disclosed publicly
- Dec 8, 2023: Chaitin Research Lab successfully reproduces the exploit
- Dec 9, 2023: Emergency advisory published by Chaitin SRC
References
Stay patched, stay safe.
Follow us for more real-world CVE breakdowns and WAF best practices.
Join the SafeLine Community
If you continue to experience issues, feel free to contact SafeLine support for further assistance.



Top comments (0)