> About Author
Hi, I'm Sharon, a product manager at Chaitin Tech. We build SafeLine, an open-source Web Application Firewall built for real-world threats. While SafeLine focuses on HTTP-layer protection, our emergency response center monitors and responds to RCE and authentication vulnerabilities across the stack to help developers stay safe.
Apache Tomcat is a widely used open-source Java Servlet container and web server, commonly deployed for enterprise-grade web applications.
In December 2024, Apache released a security patch addressing a high-risk vulnerability—CVE-2024-50379—which could allow remote code execution (RCE) under specific, non-default configurations on Windows servers. Exploits are already public, and affected users are strongly advised to patch immediately.
Vulnerability Overview
CVE-2024-50379 stems from inconsistencies between the Windows file system and Tomcat's handling of case sensitivity in file paths.
An attacker can bypass Tomcat's path validation logic by exploiting this case mismatch, turning an otherwise non-executable file (like a .JSP with altered casing) into one that Tomcat will parse and execute.
If the following conditions are met:
- The
readonlyparameter inconf/web.xmlis set tofalse(non-default), - HTTP
PUTmethod is allowed, - Server is running on Windows,
then an attacker can:
- Upload a malicious
.jspfile via PUT, - Use race conditions to repeatedly request it,
- Trigger Tomcat to execute the payload.
This results in unauthenticated remote code execution, allowing full control over the server.
Impact
A successful exploit could lead to:
- Remote command execution
- Full server compromise
- Data leaks, service disruption
- Potential ransomware or malware deployment
Exploit status: Public POC/EXP available
Severity: Critical
Authentication required: None
User interaction required: None
Bulk exploitability: Yes
Platform: Windows only
Fix complexity: Low (vendor patch available)
Affected Versions
- Apache Tomcat 11.0.0-M1 to < 11.0.2
- Apache Tomcat 10.1.0-M1 to < 10.1.34
- Apache Tomcat 9.0.0.M1 to < 9.0.98
Mitigation & Patch Guidance
Official Fix
Upgrade to the patched versions:
- 11.0.2
- 10.1.34
- 9.0.98
Download the updated release from the Apache Tomcat official site.
Temporary Workarounds
If patching is not immediately possible:
- Set
readonlytotrueinconf/web.xml, or comment it out. - Disable the PUT method in your web.xml or server configuration.
- Avoid exposing Tomcat directly to the internet.
- Deploy a Web Application Firewall (WAF) like SafeLine to block suspicious uploads.
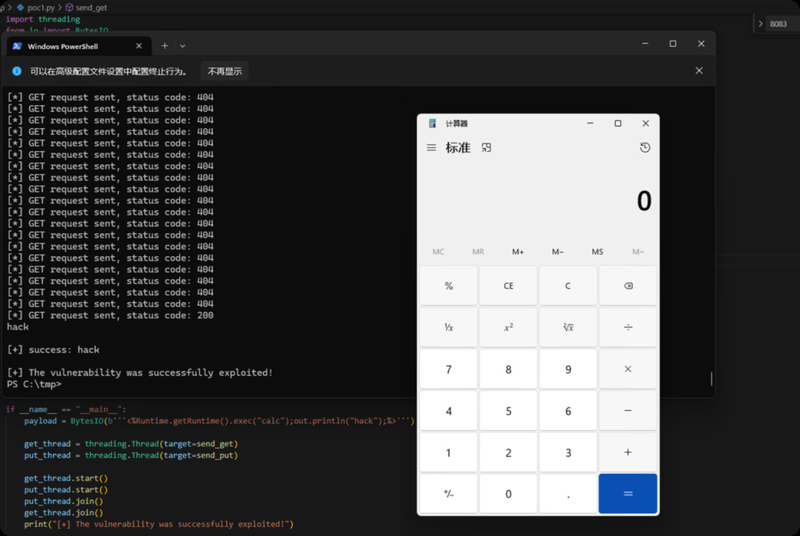
Reproduction
Exploit Status and Detection
- POC: Publicly available
- SafeLine WAF: Detects exploitation behavior by default
- Other tools:
- Yuntu: Supports fingerprinting and detection
- Dongjian: Scheduled to support CVE-2024-50379 this week
- Quanxi: Detects suspicious PUT-based WebShell uploads
Timeline
- December 17, 2024 — Vulnerability publicly disclosed
- December 18, 2024 — Vulnerability reproduced by Chaitin Security Lab
- December 18, 2024 — Security advisory published
References
If you're running Apache Tomcat on Windows and have enabled PUT or changed default configurations, apply the patch as soon as possible. Public exploits are already available, and attackers are actively scanning for vulnerable systems.
For real-time protection, consider using SafeLine WAF, an open-source web application firewall built for modern threats.



Top comments (0)