> About Author
Hi, I'm Sharon, a product manager at Chaitin Tech. We build SafeLine, an open-source Web Application Firewall built for real-world threats. While SafeLine focuses on HTTP-layer protection, our emergency response center monitors and responds to RCE and authentication vulnerabilities across the stack to help developers stay safe.
Apache RocketMQ is a popular open-source distributed messaging and streaming platform. It’s widely used for asynchronous communication, application decoupling, system integration, big data, and real-time computing because of its scalability and low latency.
Recently, a critical Remote Command Execution (RCE) vulnerability (CVE-2023-37582) was disclosed and patched in RocketMQ. Unfortunately, our research shows that many systems remain unpatched and publicly exposed.
To help the community, we’ve released X-POC (remote detection) and CloudWalker (local detection) tools, which are free to use and can quickly identify whether your deployment is vulnerable.
Vulnerability Overview
If the RocketMQ NameServer component is exposed to the internet without authentication, an attacker can exploit the configuration update feature to execute arbitrary commands as the RocketMQ system user.
Unlike CVE-2023-33246, which targeted other components, this vulnerability specifically impacts the NameServer service (default port 9876).
If NameServer is accessible and authentication is disabled, attackers can achieve RCE without additional conditions.
⚠️ Even if you’ve upgraded to the latest patched version, we strongly recommend enabling authentication on Broker and NameServer components. Without it, unauthorized configuration changes could still disrupt services.
Detection Tools
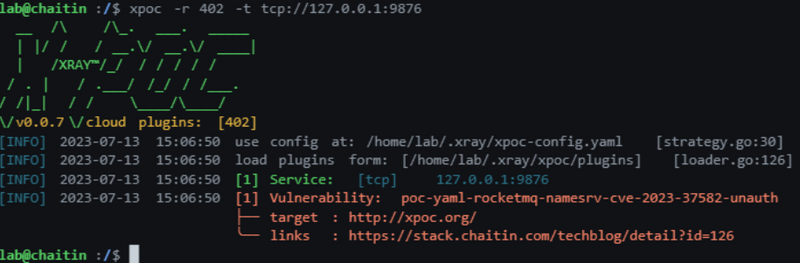
1. X-POC Remote Detection Tool
Run the following command:
xpoc -r 402 -t tcp://127.0.0.1:9876
Get the tool:
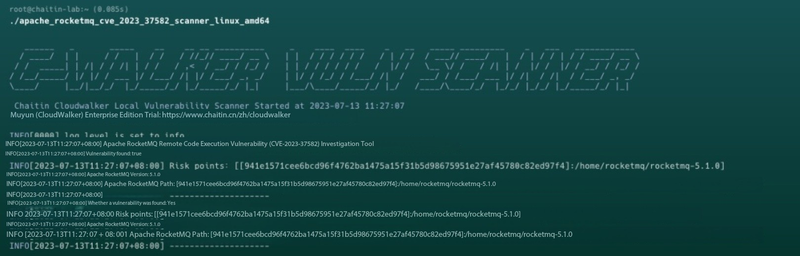
2. CloudWalker Local Detection Tool
Run a safe local scan with:
./apache_rocketmq_cve_2023_37582_scanner_linux_amd64
Get the tool:
Affected Versions
- RocketMQ < 4.9.7
- RocketMQ < 5.1.2
Mitigation & Fix
Temporary Mitigation:
Enable authentication to ensure only authorized users can access and manage RocketMQ services.
Permanent Fix:
- Upgrade RocketMQ 4.x to 4.9.7+
- Upgrade RocketMQ 5.x to 5.1.2+
References:
Security Product Support
- YunTu: Supports RocketMQ fingerprinting and PoC-based detection.
- DongJian: Allows custom PoC-based detection.
- QuanXi: Released a rule update package for exploit detection.
- CloudWalker: Users on platform version 23.05.001+ can download the emergency vulnerability library update EMERVULN-23.07.013 for detection under the "Vulnerability Emergency" module.
Timeline
- July 12: Vulnerability publicly disclosed
- July 12: Exploit reproduced by Chaitin emergency response lab
- July 13: Advisory published by Chaitin Security Emergency Response Center
Final Thoughts
CVE-2023-37582 is a serious reminder of how dangerous unauthenticated exposure can be. Even if you’ve patched, make sure authentication is enforced across all components.
Unprotected RocketMQ NameServers can easily become an attacker’s entry point.
If you haven’t yet, run the detection tools now, patch immediately, and lock down your environment.
Join the SafeLine Community
If you continue to experience issues, feel free to contact SafeLine support for further assistance.



Top comments (0)