When your website or app is behind Cloudflare, all incoming requests appear to come from Cloudflare’s IP addresses rather than your visitors’ original IPs. To ensure your SafeLine WAF doesn’t mistakenly block legitimate traffic, you should whitelist Cloudflare’s official IP ranges.
Why Whitelist Cloudflare IPs?
- Avoid false positives: Ensures your WAF doesn’t block Cloudflare’s reverse proxy servers.
- Improved performance: Reduces unnecessary filtering on trusted network traffic.
- Essential for CDN and security services: Many Cloudflare features (e.g., DDoS mitigation, caching, WAF) require your backend to trust their IPs.
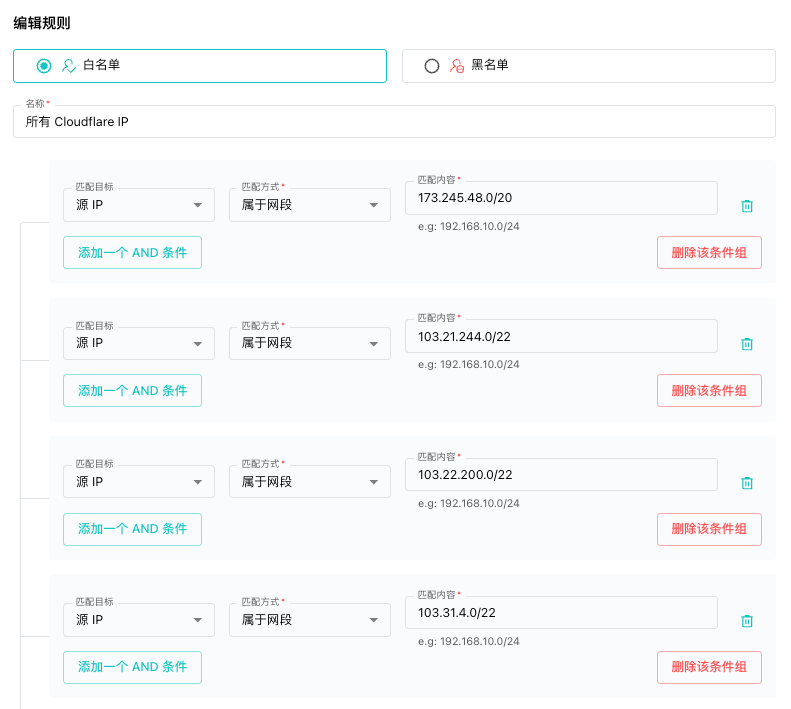
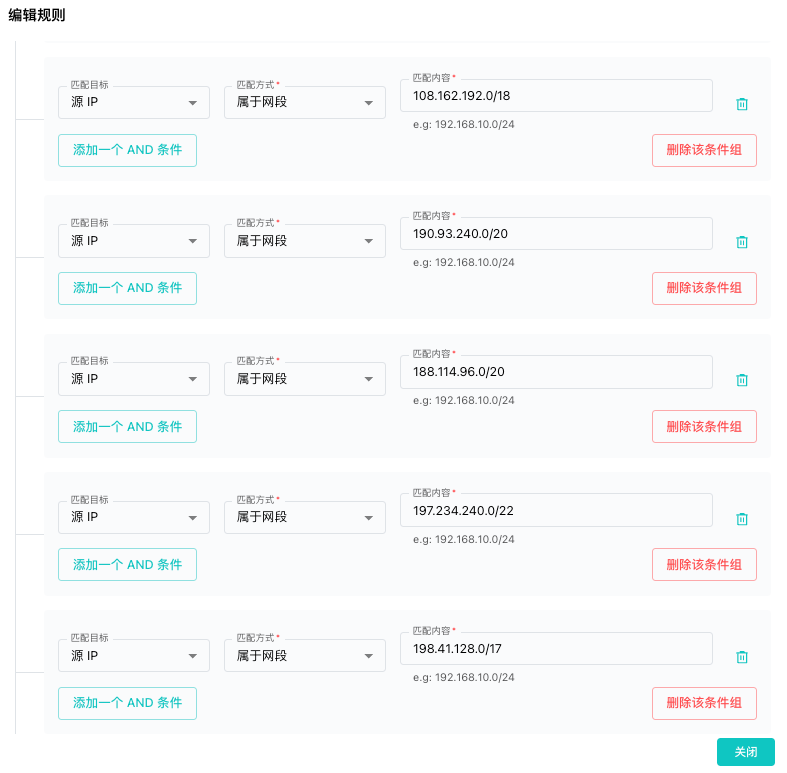
SafeLine WAF Rule Example
Rule library snapshot:
- Whitelist rules: 1
- Blacklist rules: 0
- SafeLine version supported: 7.3.0 and above
Rule details:
- Type: Whitelist
- Condition: Allow requests from all IP ranges published by Cloudflare
Cloudflare regularly updates its IP ranges, so it’s best practice to check their official list and update your SafeLine configuration accordingly.
Official source: https://www.cloudflare.com/ips/
How to Implement in SafeLine
- Go to the SafeLine WAF management console.
- Create a new whitelist rule.
- Add Cloudflare’s IP ranges (both IPv4 and IPv6) as conditions.
- Save and deploy the rule.
- Periodically review Cloudflare’s IP list for updates.
Join the SafeLine Community
If you continue to experience issues, feel free to contact SafeLine support for further assistance.



Top comments (1)
Some comments may only be visible to logged-in visitors. Sign in to view all comments.