When using a WAF, it's common to run into false positives—legitimate traffic being blocked due to strict security checks. This often happens in complex business environments where default rules don’t fully align with the application’s behavior.
In SafeLine WAF, the best way to resolve this is by configuring custom rules—either adding whitelists to allow specific traffic or blacklists to block malicious patterns.
Many users think their blacklist/whitelist configs “don’t work,” but over 95% of the time, it’s just a misconfiguration.
Many users have run into issues with custom rule configuration in SafeLine—especially when trying to fine-tune blacklists and whitelists. This guide will walk you through the logic behind SafeLine’s custom rule system and help you avoid common mistakes.
How to Blacklist a Specific URL
Let’s say we want to block access to the following test URL:
http://xxx.xxx.xxx.xxx:16666/login/123
There are 4 common methods to match this path in SafeLine:
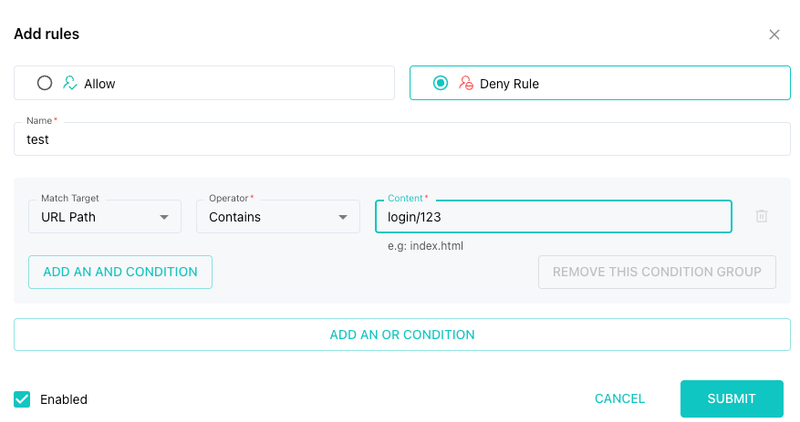
1. Partial Path Match (Recommended for Simplicity)
This is the most straightforward method. As long as the configured string appears anywhere in the path, it will match.
Examples of what you can use:
123login/login/123
✅ Flexible and ideal for most use cases.
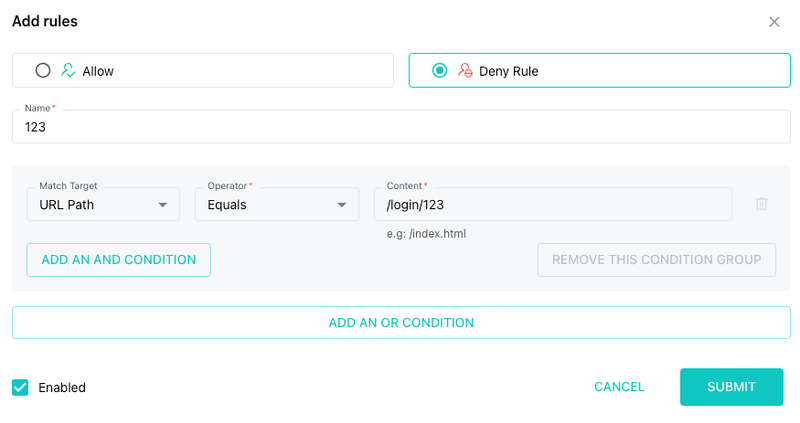
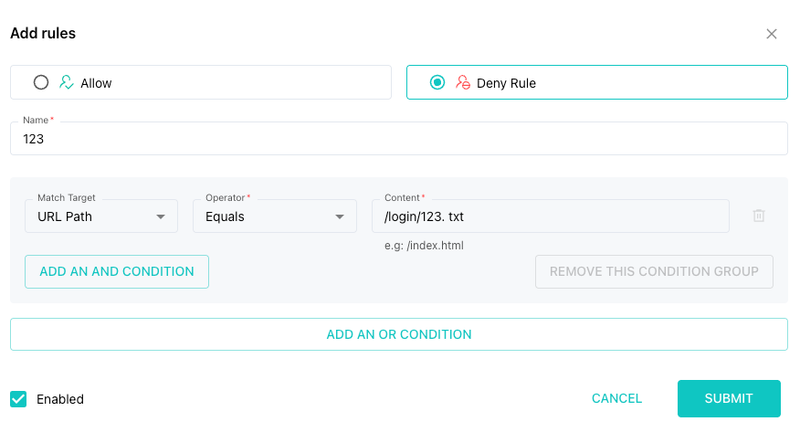
2. Exact Path Match
Use this if you want to match the entire path exactly. Be careful—this method is more rigid.
Example:
/login/123
If the path has query strings or extra segments (e.g., /login/123.txt), it won’t match unless fully specified.
⚠️ Use with caution, especially for dynamic URLs.
3. Prefix Match
This method matches any path that starts with your configured value.
Example:
-
/loginwould match/login/123,/login/test, etc.
Great for matching route groups.
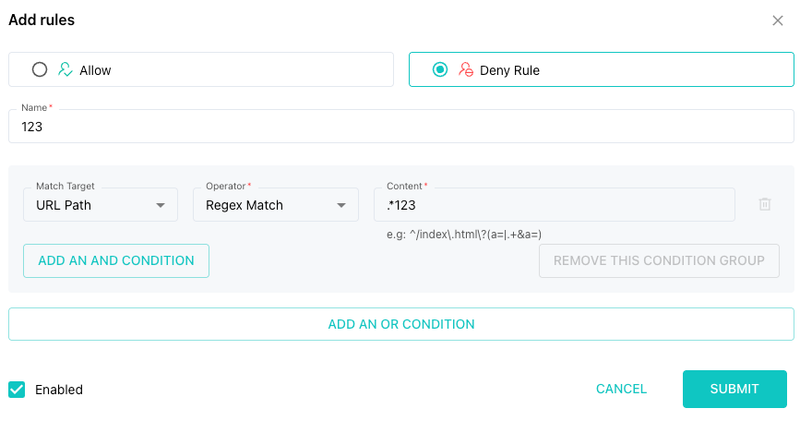
4. Regex Match
If you need fine-grained control, you can use regular expressions.
Examples:
- Match any path ending in digits:
.*123$
- Match if
123appears anywhere:.*123.*
Useful for complex URL patterns or number-based paths.
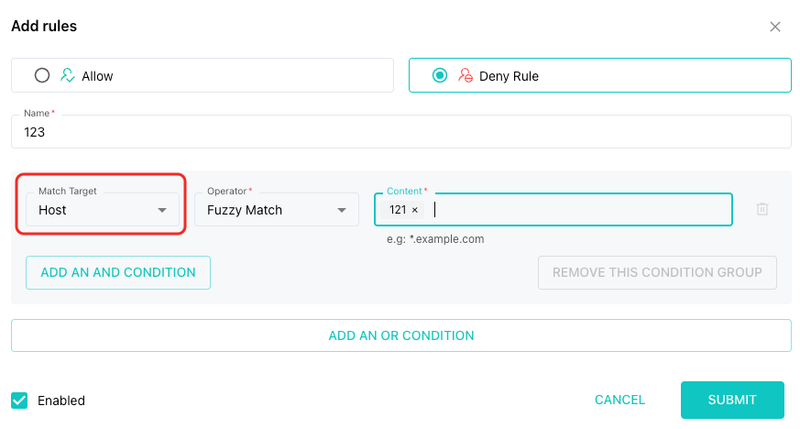
Host Match (Fuzzy Match)
Besides path, you can also match based on hostnames or IPs. SafeLine performs fuzzy matching, so partial strings work too.
Example:
- Simply use
xxx.xxx.xxx.xxxto target a specific IP.
No need to specify the full host unless required.
Don’t Let Browser Caching Fool You
While testing rules, some users get confused because their requests don’t seem to be blocked—even after correctly setting the rule.
In most cases, it’s just browser caching.
Pro Tip:
- Open DevTools (press
F12) - Go to the "Network" tab
- Check “Disable cache”
- Keep DevTools open while testing
Otherwise, your browser may not send a new request to SafeLine at all.
Final Thoughts
Configuring custom rules in SafeLine isn’t hard once you understand the matching logic. Take time to test and iterate. It’s often just a few characters that make or break a rule.
If you're using the SafeLine Community Edition, mastering these configurations is crucial for smooth protection and performance.






Top comments (0)