> About Author
Hi, I'm Sharon, a product manager at Chaitin Tech. We build SafeLine, an open-source Web Application Firewall built for real-world threats. While SafeLine focuses on HTTP-layer protection, our emergency response center monitors and responds to RCE and authentication vulnerabilities across the stack to help developers stay safe.
Weaver e-cology, a widely used collaboration and office automation (OA) platform in China, was recently found vulnerable to a frontend file upload flaw that can lead to remote code execution (RCE).
Weaver has already released a patch to fix the issue. Our team at Chaitin Security Response Center analyzed and reproduced the vulnerability and released detection tools to help admins verify whether their deployments are affected.
Vulnerability Overview
- Type: Arbitrary File Upload → RCE
- Severity: High
- Attack Vector: Network (unauthenticated)
- Scope: Exploitable only in internal networks and under cluster deployment mode
- Impact: Remote command execution on the affected OA server
⚠️ Note: The exploit surface is very limited. Only Weaver e-cology deployments using cluster mode are impacted. Most standard single-node setups are not affected.
Detection Tools
To make it easier for sysadmins and security teams to check exposure, Chaitin has published two tools:
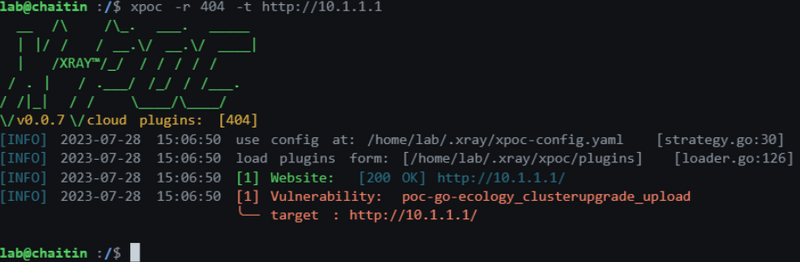
X-POC (Remote Detection)
xpoc -r 404 -t http://10.1.1.1
Download:
CloudWalker (Local Detection)
./weaver_ecology_frontend_file_upload_vuln_scanner_windows_amd64.exe
Download:
Affected Versions
-
e-cology 9 → Patch version <
10.58.3 -
e-cology 8 → Patch version <
10.58.3
Solutions
Official Patch
Weaver has released updated patches.
👉 Download from official site
Temporary Mitigation
- Restrict network access with ACLs, only allowing trusted IP ranges.
- Avoid exposing the system directly to the internet unless necessary.
Product Support
- YunTu → Supports fingerprinting of Weaver products by default.
-
DongJian → Emergency update package
6.12.3to be released July 31. - SafeLine WAF → Virtual patch released to block exploitation attempts.
- QuanXi → Rule update package released, supports detection of exploitation.
-
CloudWalker → Users on 23.05.001+ can download emergency vuln intel pack
EMERVULN-23.07.028for detection.
Timeline
- 2025-07-25 → Weaver publishes advisory and patch
- 2025-07-26 → Chaitin emergency team receives intelligence
- 2025-07-27 → Vulnerability analysis and reproduction completed
- 2025-07-28 → Chaitin Security Response Center publishes advisory
TL;DR
- Weaver e-cology cluster deployments had a file upload → RCE flaw.
- Exploitable only in internal networks, reducing real-world risk.
- Patch
10.58.3fixes the issue — update immediately. - Detection tools (X-POC, CloudWalker) are available for admins to verify exposure.
- SafeLine WAF users are already protected via virtual patch.
Join the SafeLine Community
If you continue to experience issues, feel free to contact SafeLine support for further assistance.



Top comments (0)