> About Author
Hi, I'm Sharon, a product manager at Chaitin Tech. We build SafeLine, an open-source Web Application Firewall built for real-world threats. While SafeLine focuses on HTTP-layer protection, our emergency response center monitors and responds to RCE and authentication vulnerabilities across the stack to help developers stay safe.
Weaver e-cology OA is a widely used collaboration platform in China, supporting HR, finance, administration, and mobile office functions.
Recently, Weaver released a patch addressing a critical XXE (XML External Entity) vulnerability. Chaitin’s emergency response team has confirmed the bug and warns that many public-facing systems remain unpatched.
To help defenders, Chaitin has released both X-POC (remote detection) and CloudWalker (local detection) tools, which are freely available.
Vulnerability Description
The flaw comes from incomplete input filtering in one feature of e-cology. Attackers can craft malicious XML payloads that bypass the original fix, leading to:
- Directory listing
- Arbitrary file read
- Possible system admin takeover
Chaitin’s researchers confirmed that only the incremental patch 10.58.1 fixes the issue. The full patch 10.58.1 does not include the relevant code.
Detection Tools
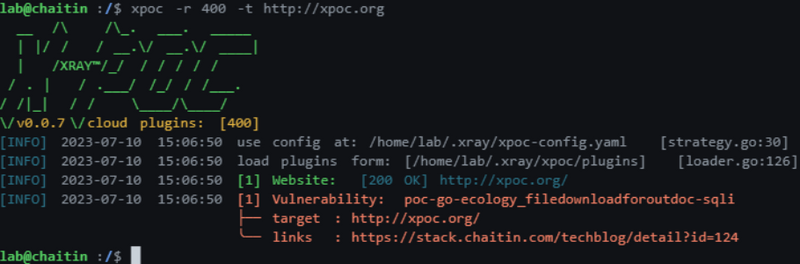
X-POC Remote Scanner
xpoc -r 401 -t http://xpoc.org
Get it here:
CloudWalker Local Scanner
Run the binary locally for safe scanning:
weaver_ecology_xxe_vuln_scanner_windows_amd64.exe
Download:
Affected Versions
- e-cology 9.x
- Incremental patch versions below 10.58.1
Mitigation & Fix
Temporary Mitigation:
- Restrict external access; avoid exposing the system to the internet unless necessary.
Permanent Fix:
- Install the incremental patch 10.58.1 (the full patch 10.58.1 alone is insufficient).
Product Support
- YunTu: Built-in fingerprint detection + PoC validation
- DongJian: Supports PoC-based detection
- SafeLine WAF: Detects and blocks exploitation attempts by default
- QuanXi: Detects exploitation attempts by default
- CloudWalker: Users on platform version ≥ 23.05.001 can upgrade to EMERVULN-23.07.012 for detection support
Timeline
- July 11 — Chaitin obtained vulnerability intelligence
- July 12 — Vulnerability reproduced and analyzed
- July 12 — Official advisory published
References
- Weaver official patch download: Weaver Security Center
⚠️ If you’re running Weaver e-cology OA, patch immediately.
Exposed systems remain at high risk of exploitation. SafeLine WAF and Chaitin’s detection tools can help defend against real-world attacks.
Try It Yourself
Don’t just take our word for it. Try SafeLine and test it against real-world payloads.
- GitHub: https://github.com/chaitin/SafeLine
- Docs: https://docs.waf.chaitin.com/
- Discord Community: https://discord.gg/dy3JT7dkmY



Top comments (0)