As modern cyber threats become more sophisticated, traditional rule-based firewalls are struggling to keep up. That’s where SafeLine comes in — a powerful, self-hosted WAF designed to intelligently analyze and scrub malicious traffic in real time.
In this article, we explore how SafeLine’s smart traffic filtering engine works under the hood and how it helps organizations stay ahead of evolving threats like zero-days, bot attacks, and HTTP DDoS floods.
Why Traffic Filtering Still Matters
Not all traffic is good traffic.
A massive part of network security today lies in being able to detect, analyze, and block malicious traffic before it ever reaches your infrastructure. From HTTP DDoS floods to automated scanners and zero-day payloads, organizations need more than static rules — they need a WAF that can think.
What Makes SafeLine Different?
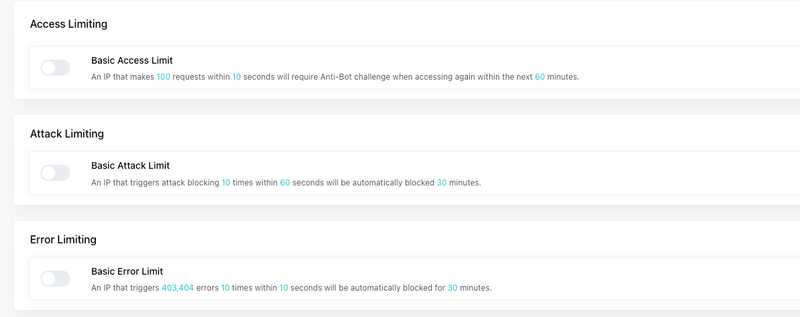
Unlike traditional WAFs that rely on hardcoded rule sets, SafeLine uses an intelligent semantic analysis engine to inspect traffic with context awareness. Here's how it works:
Semantic-Level Inspection
SafeLine goes beyond surface pattern matching. It understands the intent behind traffic — whether it’s a legitimate API call or a stealthy payload attempting path traversal or command injection. This allows it to block unknown or polymorphic attacks that would slip through regex-based filters.
Real-Time Threat Detection
SafeLine constantly monitors incoming traffic and performs inline analysis. This allows it to make split-second decisions on what should be allowed, blocked, or challenged — without introducing noticeable latency.
Automated Response at Scale
Once a threat is detected, SafeLine doesn’t just alert — it acts. Malicious requests are blocked or redirected automatically. This reduces the manual load on security teams and ensures that attacks are neutralized before they cause damage.
Continuous Learning
SafeLine adapts. It learns from both historical traffic patterns and threat intelligence to refine its detection capabilities. The longer it runs in your environment, the smarter and more accurate it becomes — minimizing false positives and catching more edge-case threats.
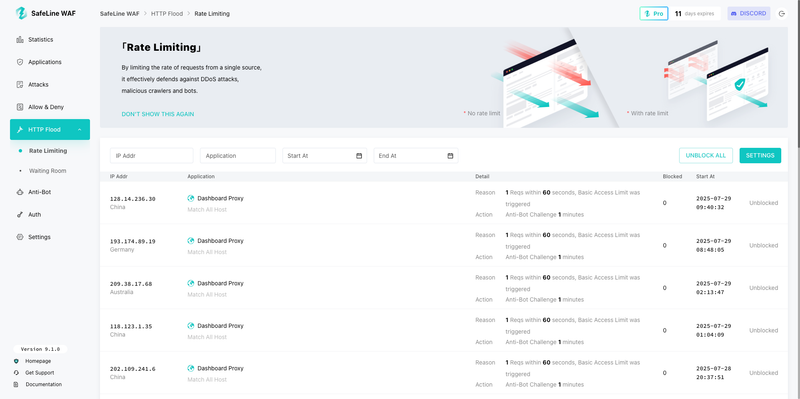
Real-World Use Case
A mid-sized company was dealing with complex traffic anomalies and frequent false alarms from its legacy WAF.
After deploying SafeLine:
- HTTP DDoS attempts were mitigated in real time.
- False positives dropped significantly.
- Even novel, zero-day-like payloads were intercepted thanks to semantic inspection.
- The IT team could finally focus on real incidents instead of chasing false alerts.
During a holiday campaign (with heavy traffic), their site stayed online and protected — no slowdowns, no outages.
Want to Try It?
SafeLine is open source and free to use. You can install it with a single command:
bash -c "$(curl -fsSLk https://waf.chaitin.com/release/latest/setup.sh)"-- --en
Official install guide: https://docs.waf.chaitin.com/en/GetStarted/Deploy
Join the SafeLine Community
If you continue to experience issues, feel free to contact SafeLine support for further assistance.



Top comments (0)