> About Author
Hi, I'm Sharon, a product manager at Chaitin Tech. We build SafeLine, an open-source Web Application Firewall built for real-world threats. While SafeLine focuses on HTTP-layer protection, our emergency response center monitors and responds to RCE and authentication vulnerabilities across the stack to help developers stay safe.
Docker Desktop, the official desktop edition of Docker, bundles the Docker Engine, CLI, Docker Compose, Notary, Kubernetes, and other developer tools into a single package for macOS, Windows, and Linux. It’s designed to simplify local container development and deployment.
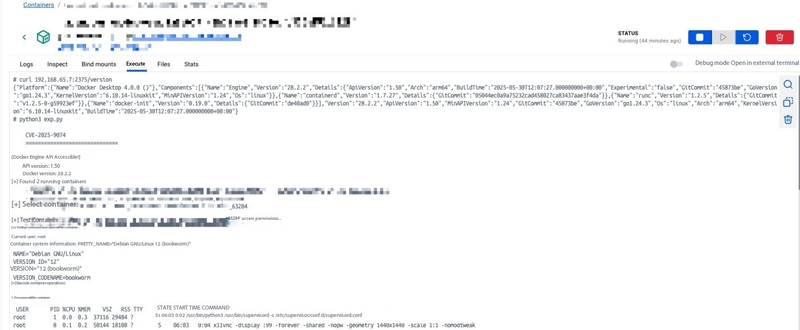
In August 2025, Docker released v4.44.3 to patch a critical vulnerability: CVE-2025-9074. This flaw allowed containers running locally to access the Docker Engine API on the host, potentially giving attackers the ability to control other containers, create new ones, manage images, and in some cases, break out of the container environment.
What Happened?
The issue stemmed from Docker Desktop’s default network configuration, which exposed the Docker daemon API at 192.168.65.7:2375 to the internal subnet without strong isolation or access control. Because this endpoint lacked proper authentication and authorization, any container running locally could talk directly to the Docker Engine via this address, regardless of whether container isolation features or the local TCP option were enabled.
Why It Matters
With access to the Docker API, an attacker can:
- Execute privileged commands from inside a container
- Create, stop, or modify containers
- Manage and pull images
- In some environments (e.g., Windows WSL), mount host file systems, potentially obtaining the same level of access as the Docker Desktop process itself.
Risk Level: High
Attack Type: Unauthorized Access
Trigger: Remote network access (local container network)
Authentication Required: None
Affected Configurations: Default settings
Exploit Availability: PoC/Exploit publicly released
Mitigation Complexity: Low – official patch available
Affected Versions
- Docker Desktop < v4.44.3
How to Fix It
Update immediately to Docker Desktop v4.44.3 or later.
Release notes and download link: https://docs.docker.com/desktop/release-notes/
Proof-of-Concept (Reproduction)
References
Join the SafeLine Community
If you continue to experience issues, feel free to contact SafeLine support for further assistance.



Top comments (0)