> About Author
Hi, I'm Sharon, a product manager at Chaitin Tech. We build SafeLine, an open-source Web Application Firewall built for real-world threats. While SafeLine focuses on HTTP-layer protection, our emergency response center monitors and responds to RCE and authentication vulnerabilities across the stack to help developers stay safe.
In July 2025, a serious file upload vulnerability was disclosed in Yonyou U8 Cloud, a cloud-based ERP platform widely used by growing and innovative businesses across Asia. The flaw allows unauthenticated attackers to upload and execute arbitrary code on the server by bypassing deserialization protection.
Due to the low exploitation barrier and severity of impact, affected users are strongly advised to patch immediately.
Vulnerability Overview
Root Cause
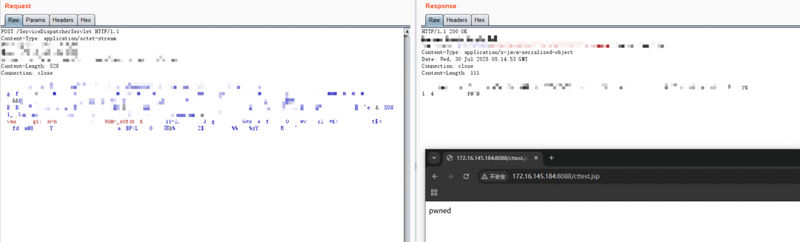
The vulnerability lies in how ServiceDispatcherServlet handles serialized user input. Improper input validation allows attackers to bypass token-based authentication. By crafting a malicious payload, they can upload a .jsp webshell to the server's web directory and gain remote code execution (RCE).
Impact
- RCE (Remote Code Execution): Attackers can execute arbitrary system commands.
- Server Takeover: Full control of the host system.
- Data Theft & System Compromise: Potential exposure of sensitive business data.
| Severity | High |
|---|---|
| Attack Vector | Remote via Internet |
| Authentication | None Required |
| Default Config | Vulnerable |
| User Interaction | None |
| Exploit Status | No public POC/EXP yet |
| Patch Available | Yes |
Affected Versions
- All versions of Yonyou U8 Cloud
Solution
Official Patch (Recommended)
Yonyou has released an official patch. Users should update immediately using the link below:
👉 Download Patch from Yonyou Security Center
Temporary Workaround
If you can’t patch right away:
- Avoid exposing the U8 Cloud system directly to the public internet.
Exploit Reproduction (POC)
Detection Tools
1. Yuntu
Supports fingerprinting Yonyou products and detects this specific PoC by default.
2. DongJian
Will support custom PoC detection starting July 30, 2025.
3. QuanXi
Will release updated detection rules by July 30, 2025.
Timeline
- 2025-07-29 – Official advisory released by Yonyou Security Center
- 2025-07-30 – Vulnerability verified and published by Chaitin Emergency Response Team
Stay informed. Stay patched. If you're running Yonyou U8 Cloud, securing your ERP environment is a matter of urgency.
Join the SafeLine Community
If you continue to experience issues, feel free to contact SafeLine support for further assistance.



Top comments (0)