Writing code is just like solving a math problem: there’re many multiple ways you can do it, but there’s only one correct result. To make sure the solution you or another developer have chosen is correct, you can carry out a code audit. We do it as a service, but you can make it yourself. This article gives insights on how to do that and what to pay attention to.
What is code auditing
Code audit is a process of examining and assessing the quality of code. It helps identify potential issues in various aspects, understand the state of the written code, its reliability and weaknesses, prevent potential problems. The result of an audit is a detailed report that specifies the state of code categories, with explanations and examples.
Evaluation criteria:
At Fora Soft, we conduct code audits based on 8 key criteria:
- Code Formatting — code organization and formatting
- Best Practices — adherence to modern standards
- Maintainability — ease of maintenance
- Performance — code efficiency and speed
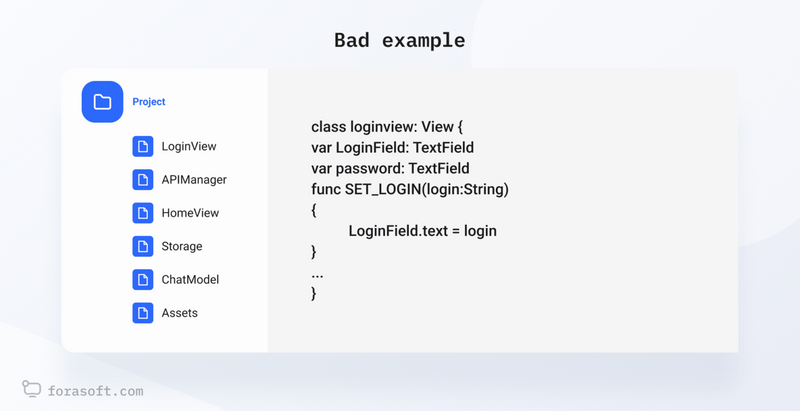
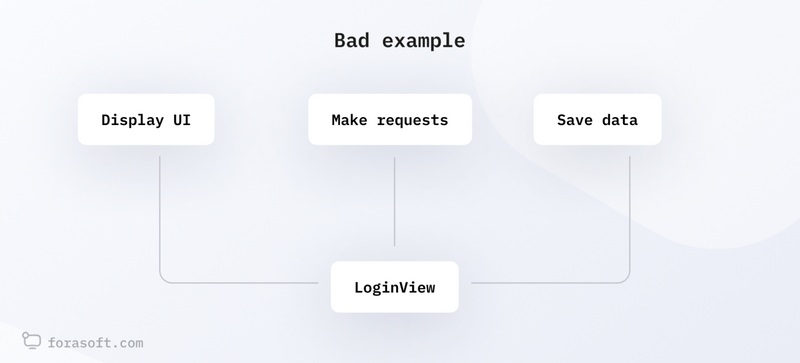
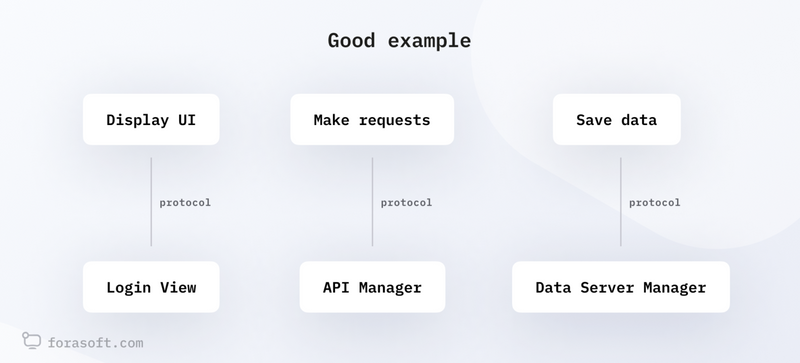
- Architecture — quality of the overall design
- Documentation — quality of accompanying documentation
- Safety — code security
- Efficiency — resource optimization Now, let’s go into each criterion in detail.
Code Formatting
This refers to how the code is written. Each programming language has its own community-accepted standards, usually multiple standards for each language. The formatting and the code writing style in a project should be consistent throughout all its parts. When evaluating formatting, we check the indentation, spacing, line breaks, and overall module structure. When evaluating style, we focus on how variables, methods, classes, and files are named and written.
Why is consistent formatting important?
Inconsistent code formatting can lead to difficulties in reading and understanding the code, affecting the speed of onboarding new developers to the project. Additional hours mean additional budget expenses.
Best Practices
In this criterion, we check if the code adheres to modern software development principles. For example, we assess whether the code follows the single responsibility principle, where each module or class is responsible for a specific task or functionality. We also evaluate how effectively the code handles errors and logs them. Another important aspect is how the specific features of the programming language are utilized in the project.
Why is this important?
Meeting this criterion ensures high-quality code and system. Otherwise, there is a risk of decreased performance, difficulties in maintenance, and implementing new functionalities into the system. Security vulnerabilities may arise, and the scalability of the project may be limited.
Maintainability
We assess how maintainable the code is, meaning whether its writing adheres to general rules that are language-independent.
Why is this important?
Software often requires constant changes, bug fixes, and additions of new features in response to evolving business or user requirements. Proper use of loops, conditions, absence of duplicated code segments, universality of written classes and functions, and their scalability make the task much easier. Otherwise, the code becomes harder to understand, more fragile, and prone to errors. Making changes or fixes will then require more time, which translates to increased expenses.
Architecture
In this category, we evaluate the modules, their cohesion, and configurability. We assess how well the code and the entire project are divided into modules or components. A good architecture should be modular, with weak coupling between modules, which simplifies system maintenance and expansion.
Why is it important?
If the code architecture is unclear, complex, and unstructured, it can hinder the process of maintaining and developing the system. Developers will face difficulties in understanding the functionality and logic of the code, as well as making changes.
Costs of fixing and modifying. Incorrect architecture may require significant changes and modifications to the code to fix issues or add new functionality. This increases development costs, time to market, and project management complexity.
Documentation
We check the quality, relevance, and presence of documentation. Documentation helps clients and future developers better understand the code and its functionality. Good documentation simplifies system maintenance, development, and integration. It usually includes:
A readme file that briefly describes the project’s essence, explains how to install and use the system, etc. It is important to include diagrams that explain the workings of complex modules.
Why is it important?
The absence of documentation poses a risk of knowledge loss, especially if there have been changes or reassignments within the development team. This hinders the understanding of the system’s operation and can lead to dependence on a limited circle of employees familiar with the code.
Security
We check the security of the code and identify vulnerabilities. Specifically:
Input data vulnerabilities. We check how user input data is handled, whether the system properly filters, validates, and escapes user input. We check for vulnerabilities such as SQL injections or script injections.
Authentication and authorization. We assess how authentication (verification of authenticity) and authorization (access control) mechanisms are implemented in the code. We check if secure password storage methods are used and if there are mechanisms to prevent password guessing or session ID guessing attacks.
Encryption and data protection. We check that confidential data (passwords, personal user information) is stored in encrypted form. We ensure that secure encryption protocols are used when transmitting data over the network.
Why is it important?
Neglecting code security increases the risk of:
- Leakage of confidential user data or violation of their confidentiality.
- System hacking or injection of malicious code. Violation of data integrity.
- Loss of access to the system or service.
- Financial losses or legal issues.
- Damage to reputation and user trust.
Efficiency
In this aspect, we examine how effectively the code utilizes system resources, its performance, and algorithm optimization. We consider factors such as execution time, whether it justifies its size, memory leaks, caching (for repeated requests), and the use of appropriate data structures and algorithms.
Why is it important?
Potential risks of not meeting this criterion may include:
- Low performance and long operation times.
- Excessive resource usage (memory, processor time, and disk space).
- Limitations in system scalability.
- Instability and unpredictable behavior of the code when handling large volumes of data or high loads.
- Deterioration of user experience and user dissatisfaction.
Outro
Code audit is not an easy task for you have to consider many parameters at once. However, it’s a necessary thing to do to make sure you’re not wasting time or money. And if you’d like some help with it, contact us. We’ll schedule a call to discuss the details.






Top comments (0)