Most users deploy SafeLine WAF to protect public web apps — but what about SafeLine’s own management console?
By default, SafeLine’s admin dashboard runs on port 9443. If this port is exposed directly to the internet, it's a potential target for scanners, bots, and brute-force attacks. That’s a risk you shouldn’t ignore.
Here’s how to use SafeLine to protect its own login portal — a clever self-defense trick that adds an extra security layer without extra tools.
⚠️ Why You Shouldn't Leave Port 9443 Exposed
Even though the admin UI is password-protected, leaving it open to the internet means:
- Attackers can scan and probe it 24/7
- Exploits or zero-days could be attempted
- Admins have no visibility unless logs are manually checked
A more secure setup is to route access to the admin panel through SafeLine itself — just like any other protected app.
🔧 How to Harden SafeLine’s Admin Console
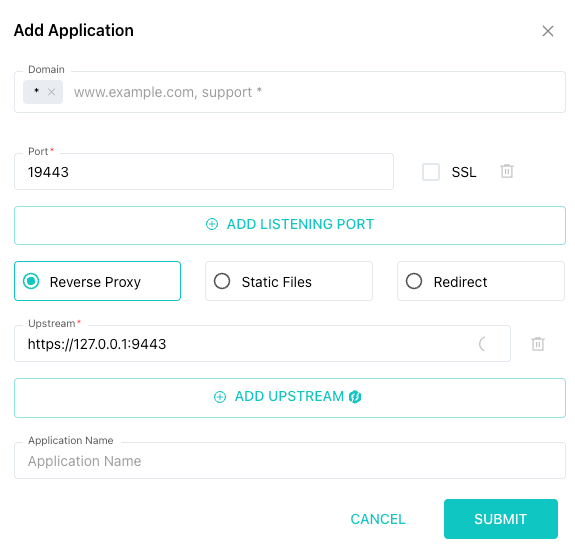
Step 1: Add a New Site in SafeLine
Go to the SafeLine dashboard and create a new application to protect.
-
Internal target:
https://127.0.0.1:9443 -
External port: Choose something like
19443to avoid conflicts
This effectively puts SafeLine’s own dashboard behind its WAF.
Step 2: Update Your Server’s Firewall or Security Group
To avoid direct exposure:
- ❌ Close port
9443in your security group or firewall - ✅ Open the new external port
19443(or your chosen value)
Step 3: Test It
Now try accessing SafeLine:
- ✅
https://your-server-ip:19443— should work via SafeLine - ❌
https://your-server-ip:9443— should be blocked completely
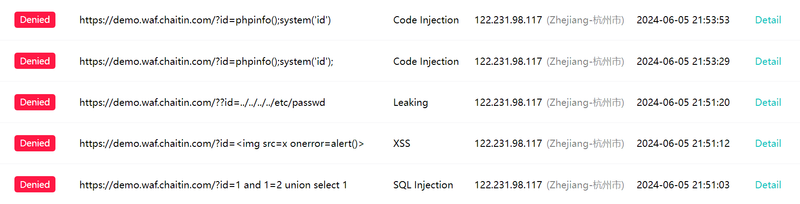
Step 4: Confirm SafeLine is Blocking Malicious Requests
Try running a simple attack pattern against 19443 — like an SQL injection or admin fuzz. You should see SafeLine detect and block it:
This proves SafeLine is now actively guarding its own admin panel — a neat example of defensive recursion.
💡 Final Thoughts
This setup isn’t just cool — it’s practical. By placing SafeLine’s own admin interface behind itself, you:
- Reduce attack surface
- Gain full audit logging of access attempts
- Get real-time protection without extra software
If you're running SafeLine in production or even just testing it in public environments, locking down port 9443 should be your first move.
Useful Links




Top comments (0)