Looking for a free, open-source way to protect your web applications from attacks like XSS, SQLi, and RCE? Here are five top-tier WAFs you can deploy today.
A Web Application Firewall (WAF) sits between users and your web server, analyzing incoming HTTP requests and blocking malicious payloads before they reach your application.
WAFs are commonly used to defend against:
- SQL Injection (SQLi)
- Cross-Site Scripting (XSS)
- Cross-Site Request Forgery (CSRF)
- Command injection
- DDoS and automated bot attacks
In this post, we’ll focus on open-source WAFs—those you can self-host, audit, customize, and scale. Whether you're securing a personal project or an enterprise-grade app, these WAFs offer powerful protection without a recurring license fee.
Why Choose an Open Source WAF?
Free to use and deploy
Privacy-respecting — no need to route traffic through third-party clouds
Highly customizable — tweak rules, loggers, detection logic
Better control over updates, integrations, and architecture
Of course, you’ll need to configure and maintain them yourself—or hire someone to do it. But for many developers and teams, that tradeoff is well worth it.
The 5 Best Open Source WAFs
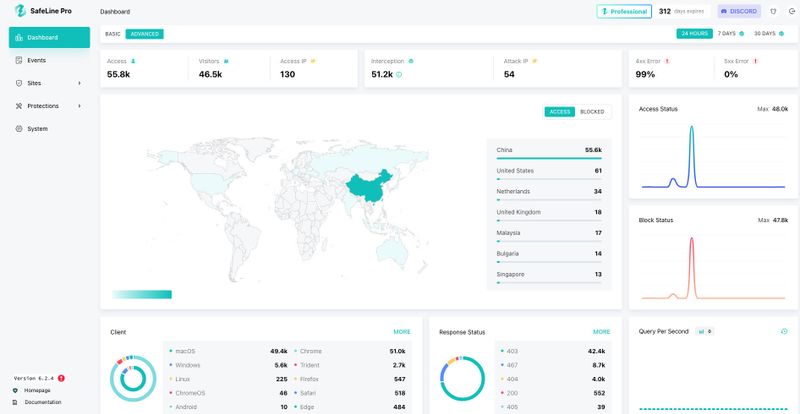
1. SafeLine
GitHub →
License: GPL-3.0
Languages: Go, C++, Perl, Lua
SafeLine is a high-performance reverse proxy WAF built on Nginx and maintained by Chaitin Tech. It detects and blocks a wide range of attacks: SQLi, OS command injection, CRLF injection, and more. It’s especially strong in anti-bot protection through:
- HTML/JS obfuscation
- IP-based rate limiting
- Semantic-aware detection engine (less reliance on rules)
You also get a modern web UI for traffic insights, real-time rule management, and monitoring — making SafeLine beginner-friendly and production-ready.
Deployment: Docker, Bash scripts
Bonus: Web dashboard included
2. open-appsec
GitHub →
License: Apache 2.0
Language: C++
Open-appsec uses machine learning models (supervised + unsupervised) to detect OWASP Top 10 vulnerabilities and zero-day attacks. It integrates with:
- Kubernetes Ingress
- NGINX
- API gateways
It deeply inspects HTTP payloads (including JSON/XML) and applies behavior-based detection. However, due to its AI capabilities, it can be resource-intensive.
Ideal for: AI-driven environments with high variability
Note: No UI, CLI-based and YAML-heavy
3. ModSecurity
GitHub →
License: Apache-2.0
Language: C++
ModSecurity is a veteran in the WAF world. It supports Apache, NGINX, and IIS, and powers many commercial WAFs. The v3 engine (libmodsecurity) decouples from Apache and improves performance.
Key strengths:
- Compatible with OWASP Core Rule Set
- Event-based detection engine
- Works well with command-line logging and alerting
Weakness: No UI, outdated documentation, steeper learning curve
Best for: Power users who want total control
4. BunkerWeb
GitHub →
License: AGPL-3.0
Language: Python
BunkerWeb is a Dockerized WAF built on NGINX. It supports:
- TLS hardening + Let’s Encrypt auto-cert
- Built-in ModSecurity integration
- Security headers
- Plugin ecosystem (e.g., ClamAV antivirus)
It features a web UI and supports deployment on Docker, Kubernetes, Azure, and Swarm. It also offers a cloud-based commercial option similar to Cloudflare WAF.
Strength: Highly configurable via plugins
Ideal for: Teams wanting UI + modular security controls
5. Coraza
GitHub →
License: Apache-2.0
Language: Go
Coraza is a modern, lightweight WAF written in Go that supports ModSecurity’s SecLang and OWASP Core Rule Set. It’s designed to be fast and embeddable, making it perfect for cloud-native and microservice environments.
Coraza doesn’t ship with a UI, but you can customize loggers and integrations easily.
Drop-in replacement for ModSecurity
Works well with reverse proxies and sidecars
Final Thoughts
Open source WAFs offer a powerful and flexible alternative to proprietary services. While they may require a bit more setup, they give you control, transparency, and strong security with no vendor lock-in.
Remember: A WAF is just one part of a complete security strategy. Regular audits, secure coding, and patching are just as critical.
Join the SafeLine Community
If you continue to experience issues, feel free to contact SafeLine support for further assistance.
Original article: https://fosspost.org/open-source-waf-web-application-firewalls



Top comments (1)
Great roundup — seriously useful if you're self-hosting anything exposed to the internet.
Just wanted to throw in a quick angle for people who run or manage modded APK distribution platforms or app indexing sites like HappyMod. Sites like that are prime targets for abuse: bot scraping, fake uploads, traffic manipulation, and exploit attempts — especially when handling user uploads or APK metadata via forms or APIs.
If you're building or managing anything similar to HappyMod’s backend, a WAF like SafeLine or BunkerWeb is a smart layer to add — especially since they're Docker-ready and give you real-time rule control. You don’t want a mod-sharing platform getting flagged for distributing malware due to a bypassed upload filter.
ModSecurity is still a classic, but honestly, the learning curve is brutal unless you’re ready to dive deep.
TL;DR — if your site handles dynamic content, user interaction, or exposed APIs (like HappyMod APK platform), open-source WAFs are a no-brainer.
Appreciate the list. Bookmarking this one.