> About Author
Hi, I'm Sharon, a product manager at Chaitin Tech. We build SafeLine, an open-source Web Application Firewall built for real-world threats. While SafeLine focuses on HTTP-layer protection, our emergency response center monitors and responds to RCE and authentication vulnerabilities across the stack to help developers stay safe.
JumpServer is a popular open-source bastion host and operations audit platform, widely adopted for its compliance with 4A standards.
In September 2023, the JumpServer team released a patch for a critical flaw: CVE-2023-42820. This bug made it possible to predict the verification code for password resets, potentially allowing attackers to hijack accounts. Combined with other flaws like CVE-2023-42819, this could escalate to full remote code execution (RCE).
What’s the Issue?
The root cause lies in an API design flaw where random number seeds were leaked, letting attackers craft malicious requests to reset passwords. By exploiting this, an unauthenticated attacker could take over admin accounts.
For defenders, Chaitin’s emergency response team has released a free detection tool to help organizations identify vulnerable assets quickly.
Detection Tool
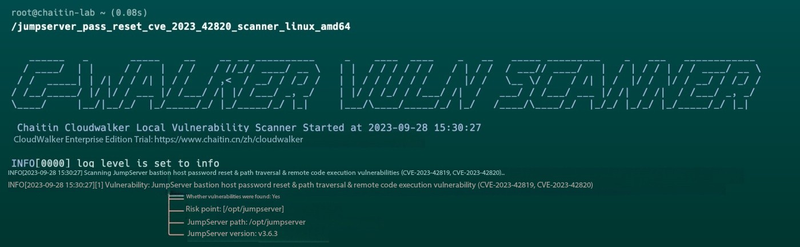
CloudWalker Local Scanner can detect vulnerable JumpServer instances.
Example usage on Linux:
./jumpserver_pass_reset_cve_2023_42820_scanner_linux_amd64
Download the tool here: https://stack.chaitin.com/tool/detail/1237
Affected Versions
- v2.24 – v3.6.4
Mitigation and Fix
Temporary Workarounds:
- Restrict access to the JumpServer admin interface using network ACLs or firewall rules. Only allow trusted IP ranges.
Permanent Fix:
-
Upgrade to the patched versions:
-
v2:
>= v2.28.20 -
v3:
>= v3.7.1
-
v2:
Official release notes and downloads:
https://github.com/jumpserver/jumpserver/releases
Vendor and Product Support
- YunTu: Supports fingerprinting and PoC-based detection for this flaw.
- DongJian: Custom PoC detection available.
- CloudWalker: For users on platform version 23.05.001+, update the emergency vulnerability library (EMERVULN-23.09.028) for detection. Others should contact technical support.
Timeline
- Sep 26: Public disclosure of vulnerability details
- Sep 27: Chaitin lab reproduces and confirms the issue
- Sep 28: Official advisory released
Join the SafeLine Community
If you continue to experience issues, feel free to contact SafeLine support for further assistance.



Top comments (0)