About Author
Hi, I'm Sharon, a product manager at Chaitin Tech. We build SafeLine, an open-source Web Application Firewall built for real-world threats. While SafeLine focuses on HTTP-layer protection, our emergency response center monitors and responds to RCE and authentication vulnerabilities across the stack to help developers stay safe.
In March 2025, a high-risk vulnerability was disclosed in the popular React-based framework Next.js, maintained by Vercel. Tracked as CVE-2025-29927, this flaw allows attackers to bypass middleware logic, which can impact authentication, security headers, and access controls—especially in apps using Edge Middleware, enabled by default.
Why It Matters
Next.js powers many AI-driven platforms and modern web applications. This vulnerability affects apps relying on middleware for authentication, redirects, and security logic.
Researchers at Chaitin Tech confirmed that the bug affects several popular AI apps in the wild. If you're using Next.js with Edge Middleware, your app could be at serious risk.
Vulnerability Overview
- CVE ID: CVE-2025-29927
- Severity: High
- Type: Logic flaw
- Trigger: Remote request
- Auth Required: No
- User Interaction: None
- Exploit Availability: Public PoC
- Fix Difficulty: Low
Root Cause
Next.js uses a special header called x-middleware-subrequest to track internal subrequests. But it does not verify whether the header comes from a trusted internal source. This allows attackers to forge the header, tricking the app into skipping middleware logic like authentication or security enforcement.
Exploitation Conditions
You're vulnerable if:
- You use Next.js middleware for auth, redirects, or header-based security.
- You're using Edge Middleware (enabled by default).
- You are on one of the affected versions (see below).
What Can Go Wrong
- Auth Bypass: Attackers can access restricted endpoints like admin panels or user APIs without logging in.
- Security Logic Skipped: CSP headers, redirects, or WAF filters implemented in middleware may be ignored.
Affected Versions
11.1.4 <= Next.js <= 13.5.6
14.0.0 <= Next.js <= 14.2.24
15.0.0 <= Next.js <= 15.2.2
Fixed Versions
14.2.2515.2.3
Mitigation Options
✅ Permanent Fix
Upgrade to the latest patched version:
🛡️ Temporary Workarounds
If you can’t upgrade immediately:
-
Strip the Header: Remove the
x-middleware-subrequestheader at the proxy or CDN level (e.g., Nginx, Cloudflare). - Use WAF Rules: Set up WAF filters (like with SafeLine WAF) to block or sanitize the suspicious header.
Proof of Concept (PoC)
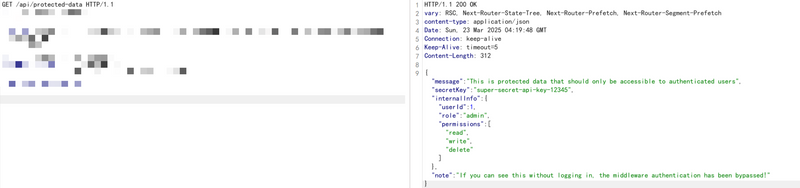
A working PoC has been published. Chaitin Security researchers confirmed the exploit by injecting a fake x-middleware-subrequest header to bypass middleware logic.
Disclosure Timeline
- Mar 23, 2025 – Vulnerability publicly disclosed
- Mar 23, 2025 – Reproduced by Chaitin Emergency Lab
- Mar 24, 2025 – Public advisory and patches released
References
- GitHub Advisory: GHSA-f82v-jwr5-mffw
Final Thoughts
This is a serious logic flaw affecting middleware behavior in Next.js. If your app relies on middleware for security-critical workflows, act now. Upgrade to the patched version or apply temporary protections until you can.



Top comments (1)
Thanks for sharing