> About Author
Hi, I'm Sharon, a product manager at Chaitin Tech. We build SafeLine, an open-source Web Application Firewall built for real-world threats. While SafeLine focuses on HTTP-layer protection, our emergency response center monitors and responds to RCE and authentication vulnerabilities across the stack to help developers stay safe.
In July 2025, Redis patched a critical vulnerability in its HyperLogLog implementation. The flaw allows remote code execution (RCE) under certain conditions, and a public proof-of-concept (PoC) exploit is already available. All users running vulnerable versions are strongly advised to upgrade immediately.
Vulnerability Overview
CVE ID: CVE-2025-32023
Type: Remote Code Execution (RCE)
Severity: High
Authentication Required: Yes
User Interaction: None
Exploitation: Remote, over the network
Exploit Maturity: Public PoC available
Default Config Exploitable: Yes
Fix Complexity: Low (patch available)
Root Cause
The vulnerability arises from an out-of-bounds write in the HyperLogLog (HLL) command handling. Specifically, an authenticated attacker can send a specially crafted string to Redis, triggering a memory corruption in either the heap or stack.
The memory corruption may then be leveraged to execute arbitrary system commands — giving the attacker full control of the Redis server process.
Affected Commands:
PFADDPFCOUNTPFMERGE
These are the core commands used for HyperLogLog operations.
Impact
An attacker with Redis command access can:
- Execute arbitrary system commands
- Take full control of the Redis server
- Leak or destroy sensitive data
- Compromise surrounding infrastructure if Redis runs with elevated privileges
Affected Versions
8.0.* < Redis 8.0.3
7.4.* < Redis 7.4.5
7.2.* < Redis 7.2.10
2.8+ < Redis 6.2.19
If you're running any of the above versions, your instance is likely vulnerable.
Recommended Fixes
Temporary Mitigation
Use Redis ACLs (Access Control Lists) to deny use of HyperLogLog-related commands:
acl setuser default -PFADD -PFCOUNT -PFMERGE
Permanent Fix
Upgrade Redis to the latest patched versions:
- 8.0.3 or higher
- 7.4.5 or higher
- 7.2.10 or higher
- 6.2.19 or higher
Download here → GitHub Releases
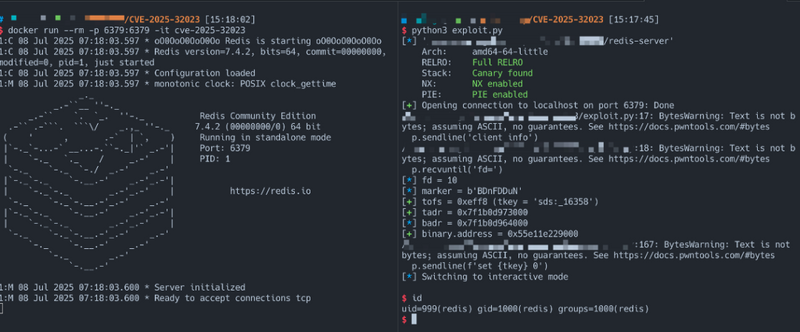
Reproduction (PoC Available)
A working proof-of-concept exploit has been published and widely circulated. If you operate Redis instances exposed to untrusted clients — especially in shared or multi-tenant environments — you are at high risk.
Ensure your server is patched and does not allow HyperLogLog commands for unprivileged users.
🔗 References
Conclusion
Redis is widely adopted in caching, session management, and real-time data processing. This vulnerability shows how even trusted data structures like HyperLogLog can become attack vectors when parsing is unsafe.
Patch now. Lock down permissions. Monitor your Red



Top comments (1)
Savastan cc - Welcome to Savastan0 cc best fresh cc shop, login to Savastan0.cc shop. official domain savastan0.cc, savastan0.biz.