When using Nextcloud, some backup processes may encounter issues where certain program files are blocked by the WAF. This can interfere with automated backups or file uploads, causing unnecessary errors.
SafeLine WAF allows you to create allowlist rules to ensure that legitimate backup operations are not interrupted. This guide explains why these rules are necessary, how they work, and how to configure them effectively.
1. Background: Why This Rule Matters
Nextcloud uses WebDAV endpoints such as:
/remote.php/dav/files/remote.php/dav/bulk/remote.php/dav/uploads/
for file storage and upload operations. During backups, multiple PUT and POST requests are made to these endpoints.
Without proper configuration, SafeLine WAF may flag some of these requests as suspicious or potentially malicious. This can result in:
- Failed or incomplete backups
- Synchronization errors
- Unexpected alerts in WAF logs
By adding allowlist rules for these endpoints, you ensure backups proceed smoothly while keeping your site protected.
2. Technical Details: How It Works
SafeLine WAF analyzes incoming requests based on:
- HTTP method (e.g., PUT, POST)
- URL/path
- Content patterns
When a request matches a rule in the denylist, it is blocked; when it matches an allowlist rule, it is allowed through even if other security checks would normally flag it.
For Nextcloud backups, allowlisting specific WebDAV endpoints ensures:
- Legitimate backup requests are not blocked
- Only specified methods and paths are permitted, minimizing security exposure
- Logs accurately reflect real threats instead of false positives
Example: A PUT request to
/remote.php/dav/files/user1/backup.zipwill be allowed if an allowlist rule is applied, while other suspicious PUT requests to unknown paths will still be blocked.
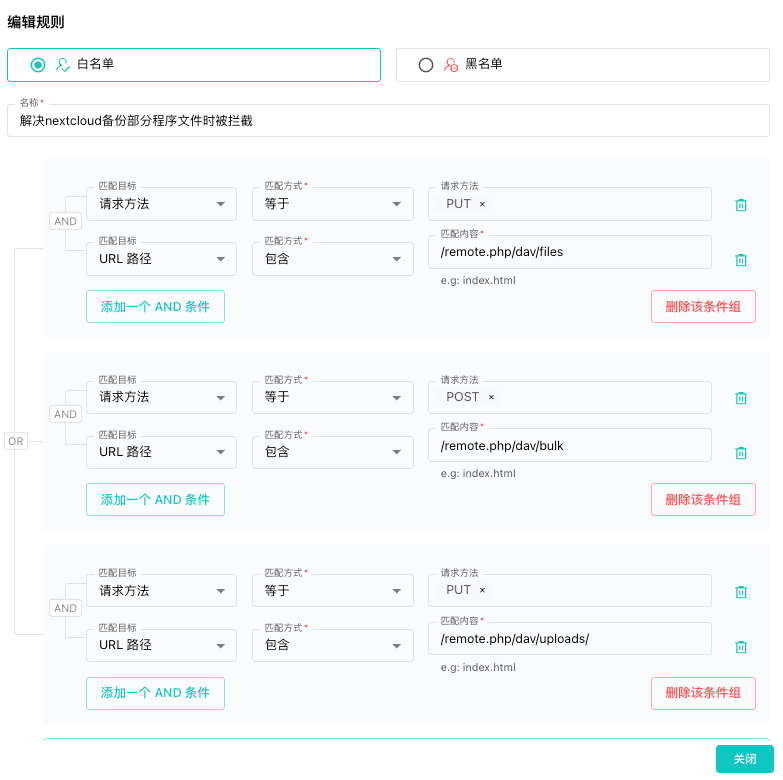
3. Step-by-Step Configuration
Follow these steps to manually add an allowlist rule for Nextcloud backups:
Access SafeLine WAF Dashboard
Log in to your SafeLine WAF account.Go to Allow & Deny
Navigate to the Allow & Deny section in the dashboard.-
Add a New Rule
Create a new allowlist rule with the following settings:-
Method & URL:
- PUT
/remote.php/dav/files - POST
/remote.php/dav/bulk - PUT
/remote.php/dav/uploads/
- PUT
- Applicable Versions: 7.3.0 and above
-
Method & URL:
You can set it up like this:
Save and Apply
Save the rule and ensure it is active.Verify
Perform a test backup and check the WAF logs to confirm that the requests are no longer blocked.
4. Best Practices
- Use Allowlist Judiciously: Only allow specific endpoints and methods that are verified as safe.
- Monitor Logs: Keep an eye on WAF logs to detect anomalies or misuse.
- Combine with Regular Security Audits: Ensure that enabling allowlist rules does not introduce new vulnerabilities.
- Update SafeLine and Nextcloud: Keep both WAF and Nextcloud up-to-date to benefit from security patches.
5. Verification & Troubleshooting
- Test Backups: Run full backup jobs to ensure files are uploaded successfully.
-
Check Logs: Look for entries related to
/remote.php/dav/paths; blocked requests indicate misconfiguration. - Adjust Rule Scope if Needed: If some legitimate requests are still blocked, refine the allowlist paths or methods.
6. Conclusion
SafeLine WAF allows you to balance security and functionality. By manually adding allowlist rules for critical Nextcloud backup endpoints, you can ensure that backup processes work reliably while keeping your site protected.
Whether you are running a personal cloud, a small business instance, or a corporate Nextcloud server, implementing these rules ensures backups complete without interference, false positives are minimized, and legitimate traffic flows smoothly.
Join the SafeLine Community
If you continue to experience issues, feel free to contact SafeLine support for further assistance.



Top comments (3)
Emergency Locksmith Leeds explains how to ensure smooth Nextcloud backups using SafeLine WAF. By integrating SafeLine Web Application Firewall, users protect their Nextcloud environment from cyber threats while maintaining reliable backup processes. Proper configuration prevents data loss, enhances security, and ensures seamless synchronization of files. Regular monitoring, encryption, and scheduled backups further safeguard critical information. Combining SafeLine WAF with Nextcloud optimizes data integrity, minimizes downtime, and provides a secure, efficient cloud storage experience.
Local locksmith provides fast and reliable services for lockouts, repairs, and key replacements, ensuring homes, offices, and vehicles remain secure. Skilled technicians handle emergency situations with speed and professionalism, as well as planned lock upgrades and installations. Available 24/7, they offer trusted solutions tailored to residential, commercial, and automotive needs. With a strong focus on customer satisfaction and safety, this locksmith service is a dependable choice for anyone seeking peace of mind and security.
tuesday motivational quotes: Protect your data protect your dreams security today brings peace tomorrow.