> About Author
Hi, I'm Sharon, a product manager at Chaitin Tech. We build SafeLine, an open-source Web Application Firewall built for real-world threats. While SafeLine focuses on HTTP-layer protection, our emergency response center monitors and responds to RCE and authentication vulnerabilities across the stack to help developers stay safe.
In December 2023, a critical remote code execution (RCE) vulnerability was disclosed in Kingdee Apusic Application Server, a widely-used Java EE enterprise application server.
The flaw stems from a backend file upload feature that can be exploited through path traversal techniques — giving attackers a way to upload malicious scripts outside of the intended directories and gain remote control over the server.
Vulnerability Overview
The core issue lies in how the backend handles file uploads:
- The upload functionality is accessible from the frontend due to poor access control.
- The server does not properly sanitize or validate file paths.
- Attackers can craft file names like
../../../../webapps/ROOT/shell.jspto upload arbitrary files to sensitive locations.
Exploitation Characteristics
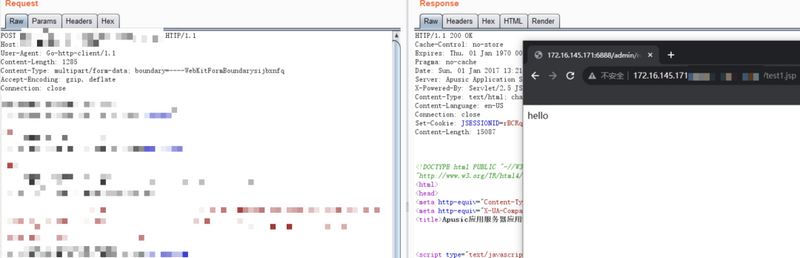
From the traffic layer, attacks can be observed as abnormal HTTP POST requests where the uploaded file includes ../ sequences — a common sign of directory traversal.
Once an attacker successfully uploads a file to the server's web root or another executable directory, they can immediately execute the payload via browser or tools like curl.
Impact
A successful exploit can result in:
- Arbitrary file uploads to any location on the server
- Deployment of web shells or backdoors
- Full server compromise
- Potential lateral movement and sensitive data leakage
This vulnerability is extremely dangerous due to:
- Minimal prerequisites for exploitation
- Public PoC availability
- Simple HTTP traffic patterns that bypass WAFs without effective file path filtering
Affected Versions
Apusic Application Server <= V9.0 SP7
If you're running any version at or below this, you should patch immediately.
Mitigation & Patch
Temporary Workaround
Until you're able to patch:
- Disable the management console and remove default web root pages if possible.
- Place the Apusic server behind internal firewalls and restrict access using IP allowlists.
- Monitor traffic for anomalous
../sequences in POST requests.
Reference:
Official Advisory and Patch
Permanent Fix
Apusic has released updated versions to address this issue. Visit the link above or contact their official support team to obtain the latest patch.
Proof of Concept (PoC)
Detection Support
The following tools and platforms have released detection or mitigation support:
- Yuntu: Fingerprint detection and PoC behavior analysis
- Quanxi: Detection rules available in latest updates
- SafeLine WAF: Rule updates released to detect and block this exploit pattern
Timeline
- Dec 7, 2023 – Official patch released by Apusic
- Dec 19, 2023 – Exploit confirmed and reproduced by researchers
- Dec 20, 2023 – Public advisory issued
References
Join the SafeLine Community
If you continue to experience issues, feel free to contact SafeLine support for further assistance.



Top comments (0)