Not all DDoS attacks are noisy. Some come disguised as normal HTTP traffic — but in massive volume. These are HTTP Flood attacks, a type of Layer 7 DDoS designed to overwhelm your web application, not your bandwidth.
In this article, we'll explain what HTTP Floods are, why traditional defenses fall short, and how Web Application Firewalls (WAFs) — especially SafeLine WAF — can help mitigate them effectively.
What Is an HTTP Flood Attack?
An HTTP Flood is a DDoS attack that bombards your web server with seemingly legitimate HTTP requests — often targeting endpoints like /login, /search, or /api/data.
Unlike volumetric attacks that aim to consume bandwidth, HTTP Floods consume application resources:
- Database queries
- Session handling
- Memory and CPU
They're hard to detect because the traffic looks "normal" — just at a massive scale.
Why Traditional Firewalls Can’t Stop Them
Most network firewalls and basic rate-limiters don’t inspect HTTP content deeply enough to catch malicious patterns. They focus on IPs and ports, not URLs, headers, or behavior.
That’s why you need an application-layer defense.
How SafeLine WAF Blocks HTTP Floods
SafeLine WAF is an open-source Web Application Firewall purpose-built to handle modern web attacks — including HTTP Floods. It provides multiple layers of intelligent protection to secure your web applications.
1. Web Attack Protection
SafeLine defends against a wide range of web attacks out of the box — including SQL injection, XSS, command injection, code injection, CRLF injection, XXE, SSRF, and path traversal. These protections are rule-based and updated regularly, so you don’t need to manually configure signatures for each threat.
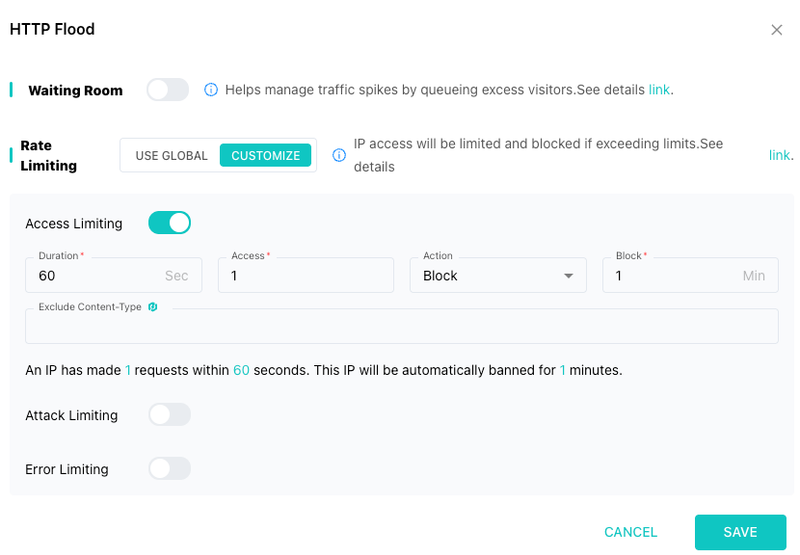
2. Rate Limiting
You can define request limits based on IP, URL, or session to throttle abusive traffic. This helps mitigate HTTP Flood attacks, brute-force login attempts, and abnormal spikes — whether they're intentional DDoS campaigns or misbehaving clients.
3. CAPTCHA Challenge
For high-risk endpoints, SafeLine can enforce CAPTCHA challenges to verify human users. Real visitors will pass seamlessly, while bots and crawlers that can’t solve CAPTCHA will be denied access.
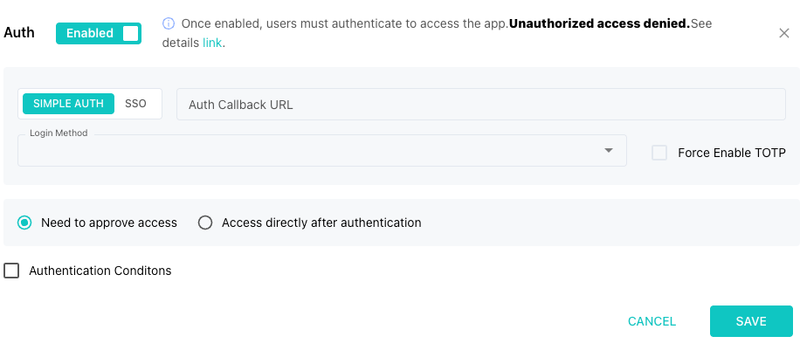
4. Authentication Challenge
In protected mode, SafeLine requires visitors to enter a password before they can access your site. This is useful for staging environments, admin panels, or internal systems that shouldn’t be exposed to the public internet.
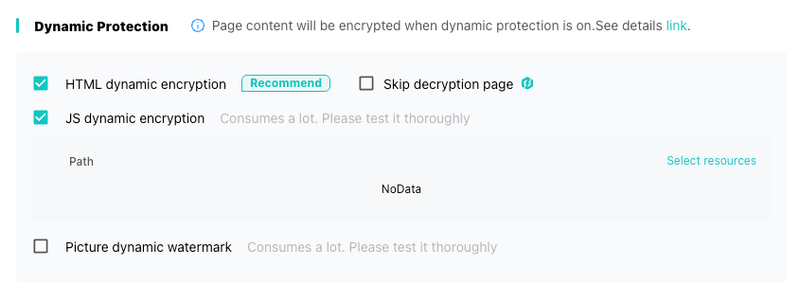
5. Dynamic HTML and JS Encryption
When enabled, SafeLine dynamically encrypts your HTML and JavaScript code on every request. This makes it significantly harder for automated tools and bots to analyze or interact with your frontend, without impacting real users.
Why Use an Open Source WAF?
SafeLine WAF gives you control without vendor lock-in:
- Free and open-source under GPL-3.0
- Runs on standard Linux servers
- Easy to integrate with existing NGINX setups
- Actively maintained and trusted in real-world production environments
Summary
- HTTP Floods are stealthy Layer 7 DDoS attacks that target your web app logic, not just your bandwidth.
- Traditional firewalls can’t stop them.
- WAFs like SafeLine are designed to inspect, rate-limit, challenge, and block malicious HTTP traffic in real time.
- If your app is on the public internet, you need a Layer 7 defense.
Join the SafeLine Community
Want to try a powerful, open source WAF?



Top comments (0)