When applying for SSL/TLS certificates using ACME protocols (such as with Let’s Encrypt), certificate authorities need to verify domain ownership. This verification is often done through requests to the special path /.well-known/.
If these requests are blocked by your WAF, the certificate application or renewal process will fail. To ensure smooth SSL certificate issuance and renewal, you need to configure SafeLine WAF to allowlist ACME requests.
1. Why This Matters
SSL/TLS certificates are critical for enabling HTTPS, protecting sensitive data, and preventing traffic interception.
However, if ACME requests to /.well-known/ are blocked, you may face issues such as:
- SSL certificate application failure
- Automatic renewal interruptions
- Websites falling back to insecure HTTP
2. How SafeLine WAF Helps
SafeLine allows fine-grained rule customization. You can add allowlist rules to let legitimate ACME traffic through while keeping malicious traffic blocked.
In this case, we add a rule to allow all requests starting with /.well-known/.
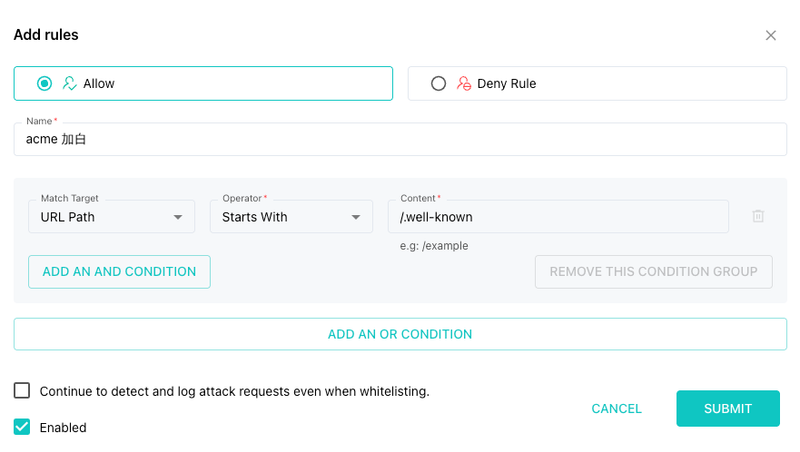
3. Adding the Allowlist Rule
To configure this in SafeLine:
Go to Allow & Deny
Navigate to the Allow & Deny section in the SafeLine dashboard.Add a New Allow Rule
Create a new allowlist rule targeting ACME requests.
You can configure it like this:
- Match Field: URL Path
- Condition: Prefix keyword
-
Value:
/.well-known
You can set it up like this.
- Save and Apply Once saved, SafeLine will allow these requests across all versions from 7.3.0 to the latest.
4. Benefits
- Seamless HTTPS: Certificates can be issued and renewed without interruptions.
- Strong Security: Only specific ACME verification requests are allowed, everything else is still filtered.
- Automated Renewals: Prevents downtime caused by failed SSL renewals.
5. Conclusion
By adding a simple allowlist rule for ACME requests in SafeLine WAF, you ensure that your HTTPS setup works flawlessly with services like Let’s Encrypt. This small configuration step keeps your certificates valid while maintaining strong protection for your site.



Top comments (1)
To allow ACME challenges for SSL certificates in SafeLine WAF, you need to configure rules that let requests to the /.well-known/acme-challenge/ path bypass strict filtering so that Let’s Encrypt or another Certificate Authority can verify domain ownership. This is usually done by creating a whitelist or exception rule in SafeLine WAF to allow HTTP GET requests to that directory without interference. Once the challenge responses are reachable, the SSL certificate issuance or renewal will succeed. It’s also important to ensure your web server is correctly serving the challenge files and that DNS records are properly pointed to the server. For administrators who manage multiple domains or government-related services like psa online appointment, setting such exceptions ensures both secure certificate management and uninterrupted access to critical online platforms