Safeline supports integration with various identity providers through the OIDC (OpenID Connect) protocol, allowing users to securely log in to applications or websites using existing identity systems. Supported identity providers include but are not limited to Keycloak, Auth0, Okta, Azure AD, etc.
{.is-info}
OIDC Protocol Introduction
OpenID Connect (OIDC) is an identity authentication layer based on the OAuth 2.0 protocol that allows client applications to verify end-user identities based on authentication results from an authorization server and obtain basic user information. OIDC enables third-party applications to securely access user information without directly managing user credentials.
Preparation
1. Select and Configure OIDC Identity Provider
Using Keycloak, a common OIDC provider, as an example, here's how to obtain the required parameters for configuration:
Keycloak Configuration
Log in to the Keycloak admin console.
Select or create a Realm.
In the left menu, click "Clients" → "Create" to create a new client.
-
Fill in the following information:
- Client ID: Specify a unique identifier for the client
-
In the "Settings" tab, configure:
- Valid Redirect URIs: Add the application's callback address, e.g.,
https://example.com/.safeline/auth/api/callback/oidc - Web Origins: Add the application address, e.g.,
https://example.com
- Valid Redirect URIs: Add the application's callback address, e.g.,
For the callback domain field, you need to append /auth/api/callback/oidc to your application URL
{.is-warning}
Save the configuration.
Switch to the "Credentials" tab and obtain the "Client Secret".
-
Record the following information:
- OIDC discovery URL:
https://{keycloak-host}/realms/{realm-name} - Client ID: The client ID you created
- Client Secret: The key obtained from the Credentials tab
- OIDC discovery URL:
2. Obtain OIDC Configuration Parameters
Regardless of which OIDC provider you use, you'll need to obtain the following information for Safeline WAF configuration:
- OIDC Discovery URL: The provider's OpenID Connect configuration information address
- Client ID: The client ID registered with the OIDC provider
- Client Secret: The client secret generated by the OIDC provider
Safeline WAF Configuration
1. Access Auth Configuration
Go to the Safeline console "Auth" → "Settings" page.
Click "Third-party Login" and select "OIDC".
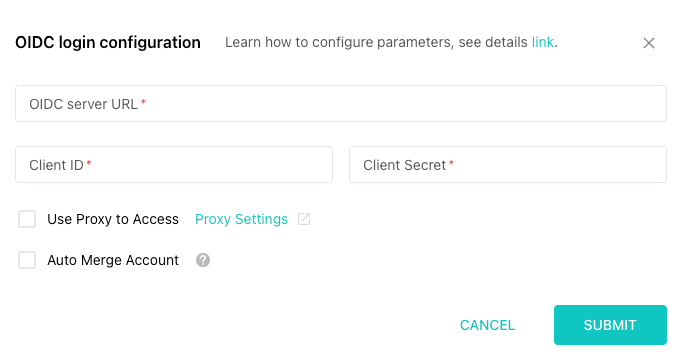
2. Fill in Configuration Information
Fill in the following information in the configuration form:
| Field | Description |
|---|---|
| OIDC Server URL | The configuration discovery URL of the OIDC provider; Safeline will automatically append .well-known/openid-configuration at the end |
| Client ID | The client ID obtained from the OIDC provider |
| Client Secret | The client secret obtained from the OIDC provider |
- After completing the configuration, click the "Submit" button to complete the binding.
3. Configure Auth Application
On the "Applications" select the application for which you want to enable OIDC login.
In the application's "AUTH - Login Methods" configuration, enable the "OIDC" option.
Save.
User Authentication Process
After enabling the "AUTH" feature and selecting OIDC login method for an application:
When users access the application, the OIDC login option will be displayed.
After clicking to log in, users will be redirected to the OIDC provider's login page.
After completing authentication on the OIDC provider's page, users will be redirected back to Safeline WAF.
-
New users authenticating for the first time will need to be approved by a Safeline administrator in the console.
- Users who pass the review will be authorized for this application and will not require further review for subsequent access.
- Users who are not approved will be blocked and unable to access the application.
User Management
On the "AUTH" → "User Management" page, you can:
- View the list of users who have been authenticated through OIDC.
- Review new users for approval.
- Manage user access permissions, including authorization and revocation.
Frequently Asked Questions
Q: Cannot redirect to OIDC provider after integration
A: Please check if the OIDC discovery URL is correct and ensure it can be accessed via a browser and returns valid JSON configuration.
Q: Callback fails after user authentication with OIDC provider
A: Please confirm that the callback address is configured correctly, including protocol (http/https), domain, and path.
Q: What scopes does Safeline request by default?
A: openid



Top comments (0)