🚀 A Powerful Web Security Tool You Can Actually Use
As someone working in cybersecurity, I’ve seen more and more dev communities talking about SafeLine WAF lately—and for good reason.
SafeLine is an open-source web application firewall (WAF) that stands out for its intelligent semantic analysis engine, a major leap beyond the traditional rule-based firewalls. The result? High detection accuracy, fewer false positives, and impressive resistance to bypass attempts.
Even better? It's easy to install (literally one click), comes with sane defaults, and is completely free to start with**—yes, really.
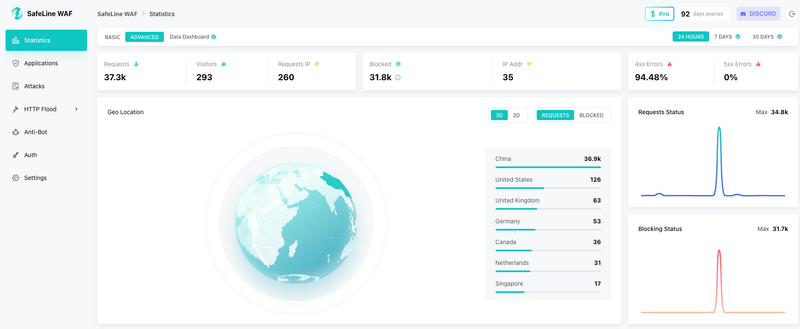
Here’s a sneak peek at what the dashboard looks like in action:
🧠 How SafeLine Works
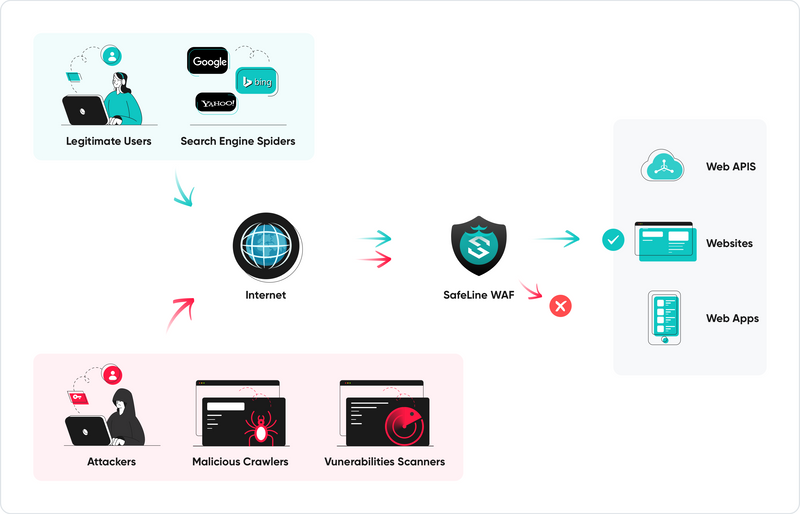
SafeLine sits in reverse proxy mode, intercepting all traffic before it reaches your web server. It analyzes and filters malicious requests in real time, only forwarding clean traffic.
🔍 Detection Workflow
The engine uses multi-layered inspection with real-time decision making. Unlike static rule-based engines, SafeLine applies semantic analysis to evaluate the intent of each request.
🧪 Quick Functional Test
Once you install SafeLine (see docs for full instructions), try a couple of simple attacks to verify it's working.
SQL Injection
http://<your-ip>:<port>/?id=1%20AND%201=1
XSS Attack
http://<your-ip>:<port>/?html=<script>alert(1)</script>
You should see SafeLine block these requests and log the incidents.
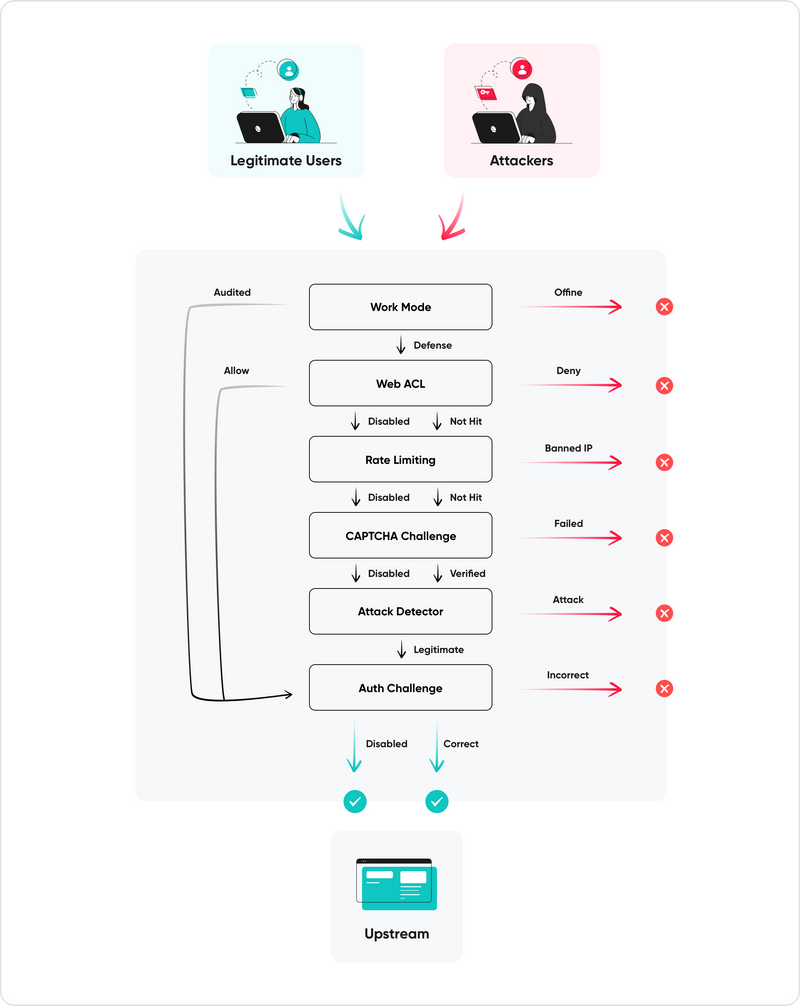
🔒 Site-Level Advanced Protection
SafeLine also supports granular, per-site protection configurations—including custom rules that remain effective even if the main toggle is off.
🧰 Core Features
SafeLine WAF is built for modern security needs. Here are the highlights:
🧠 1. Intelligent Semantic Engine
Accurately blocks attacks like SQLi, XSS, and command injection by understanding the meaning behind user input, not just matching patterns.
🔐 2. Dynamic Response Protection
Each page load delivers JavaScript and HTML in a randomized, encrypted format. This makes it incredibly hard for automated tools to parse or exploit your site.
🤖 3. Anti-Bot & Crawler Defense
Analyzes HTTP request behavior to distinguish real users from malicious crawlers. Blocks bad bots, saves resources, and protects sensitive endpoints.
🛡️ 4. Flexible Protection Policies
Built-in support for:
- IP allow/block lists
- Geo-blocking
- Custom rules
- Optional authentication layers
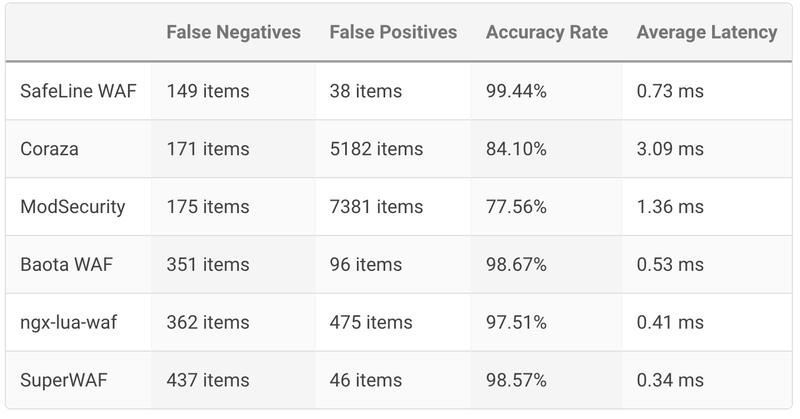
⚔️ SafeLine vs Other Open-Source WAFs
How does SafeLine stack up against alternatives?
| Feature | SafeLine | Traditional WAF |
|---|---|---|
| Semantic Analysis | ✅ | ❌ |
| Dynamic Response Protection | ✅ | ❌ |
| Easy UI & One-Click Setup | ✅ | ❌ (often CLI-only) |
| Custom Rules | ✅ | ✅ |
| Free to Start | ✅ | Varies |
Unlike some other open-source WAFs that rely solely on regex rules, SafeLine is designed to adapt and scale in real-world environments.
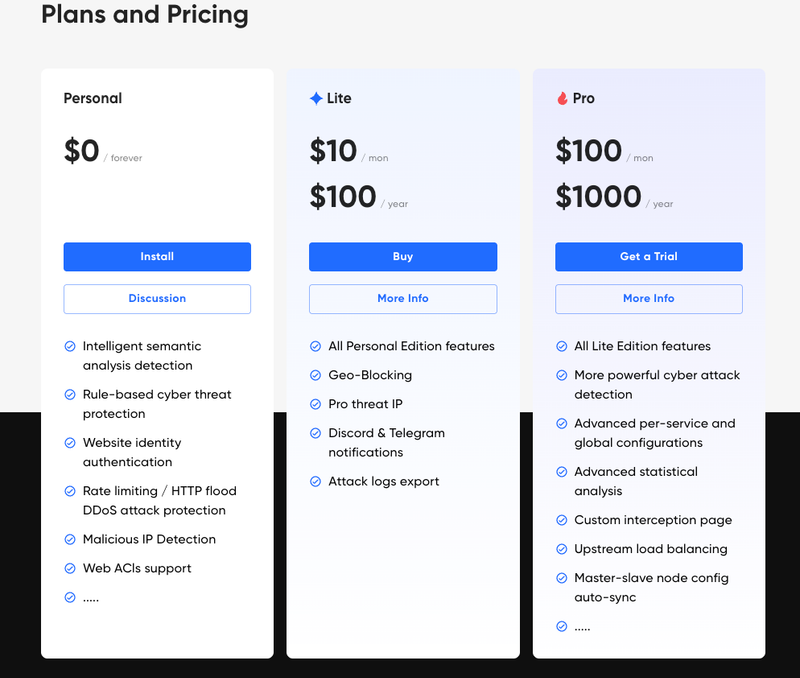
📦 Versions & Use Cases
SafeLine is available in three editions:
Personal – Free forever. Includes intelligent detection, DDoS protection, and basic IP blocking—perfect for developers and small projects.
Lite – $10/month or $100/year. Adds geo-blocking, pro-level threat IPs, messaging notifications, and log export. Ideal for small teams and more demanding use cases.
Pro – $100/month or $1000/year. Offers advanced detection, granular per-service config, load balancing, node sync, and more. Built for businesses and critical production deployments.
Whether you’re securing a blog or protecting production infrastructure, there’s a SafeLine plan to match your needs.
📚 Learn More & Get Involved
- 🌐 Official Site
- 🧑💻 GitHub Repo
- 💬 Community Forum
👋 Final Thoughts
If you’re serious about web security and tired of either bloated enterprise tools or underwhelming open-source firewalls, give SafeLine a shot.
It’s secure, modern, easy to use, and free to start with.
Got questions or want to compare notes? Join the SafeLine Community and chat with fellow developers.






Top comments (0)