> About Author
Hi, I'm Sharon, a product manager at Chaitin Tech. We build SafeLine, an open-source Web Application Firewall built for real-world threats. While SafeLine focuses on HTTP-layer protection, our emergency response center monitors and responds to RCE and authentication vulnerabilities across the stack to help developers stay safe.
Nacos, the open-source platform for service discovery and configuration, is under active exploitation due to a newly exposed Remote Code Execution (RCE) vulnerability. This flaw affects the standalone mode and stems from an unsafe SQL execution interface exposed in the admin backend.
Vulnerability Overview
In July 2024, a critical vulnerability was publicly disclosed in Nacos. Upon investigation, it was found that an attacker could exploit an insecure admin interface to execute arbitrary system commands — essentially achieving full OS-level access.
Root Cause
When Nacos runs in standalone mode, it defaults to using Apache Derby, an embedded database. Unlike MySQL or PostgreSQL, Derby can't be managed externally via JDBC. To facilitate internal operations, Nacos includes an SQL execution interface under the hood — specifically for maintenance.
However, this interface, exposed via the removal endpoint, can be abused to inject and run malicious SQL — eventually leading to RCE.
Impact
- If authentication is disabled or bypassed
- Or if attackers gain backend access with valid credentials
They can execute system-level commands using crafted SQL statements — without user interaction.
Exploit Details
- Vulnerability Type: SQL Injection → Remote Code Execution (SQLi to RCE)
- Severity: High
- Authentication Required: Only if auth is enabled
- System Requirements: Works on default configuration
- User Interaction: None
- Exploit Maturity: Public POC/EXP available
- Mass Exploitation: Yes, common tools support batch scanning
- Fix Complexity: Low — patch available
Detection
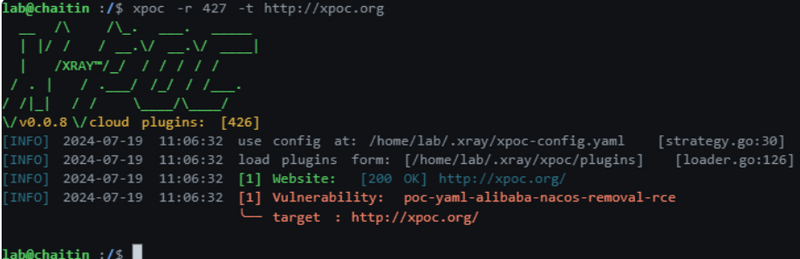
You can detect this vulnerability remotely using X-POC:
xpoc -r 427 -t http://xpoc.org
Affected Versions
Nacos < 2.4.0
Recommended Fix
Upgrade to Nacos 2.4.0 or above. In this release, the Nacos team introduced a new config option:
derbyOpsEnabled: false
This is disabled by default to prevent misuse of the SQL interface.
Temporary Mitigations
If you're unable to upgrade immediately:
- Enable authentication and set strong admin passwords.
- Switch to an external database instead of Derby.
- Use a WAF (e.g., SafeLine) to block malicious requests.
- Restrict access to internal admin URLs via firewall or URL control policies.
- Do not expose the system to the public internet if unnecessary.
Detection & Protection Support
| Product | Support Details |
|---|---|
| SafeLine | Detects exploitation behavior out-of-the-box |
| X-POC | Supports remote detection of vulnerability |
| YunTu | Fingerprint and PoC-based detection |
| DongJian | Custom PoC-based vulnerability scanning |
| QuanXi | Behavioral detection supported |
Timeline
- July 15 – Vulnerability identified and verified by Chaitin Tech
- July 15 – Internal analysis and reproduction completed
- July 15 – Customers notified by Chaitin Security Response Center
- July 19 – Official patch released by Nacos team
- July 19 – Public advisory issued
Reference
Final Note
If you're running Nacos in standalone mode with Derby enabled — patch immediately or take it offline. The exploit is public, easy to automate, and already being scanned in the wild.
If you rely on Nacos in production, consider adding a WAF like SafeLine to strengthen protection against similar backend interface abuse.



Top comments (0)