Sensitive version control and config files like .git, .svn, .htaccess, and shell history files should never be exposed over the web. If left unprotected, they can leak credentials, internal repo details, or other private data.
SafeLine WAF provides a simple but effective ruleset to block any direct HTTP access to these files, making it a must-have for homelab users and self-hosted environments.
Why Is This Important?
-
Source code exposure: Attackers can download your entire repo if
.gitis accessible. -
Server configuration leaks: Files like
.htaccessor.bash_historycan reveal system settings or secrets. - Reconnaissance protection: Stops bots and scanners from mapping your internal structure.
The Rule in SafeLine
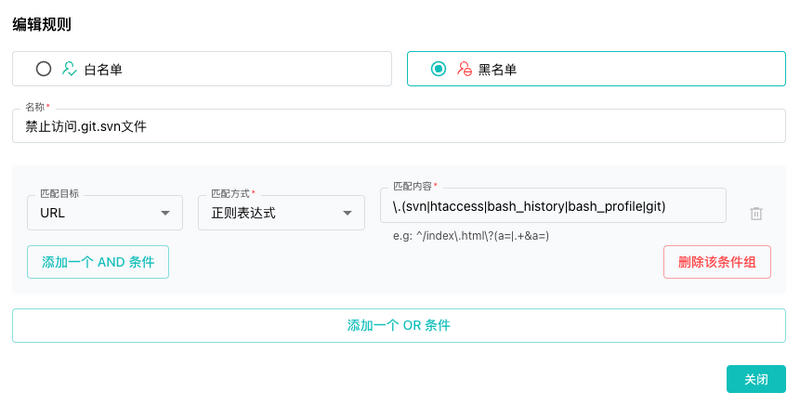
This SafeLine ruleset (available for v7.3.0 and above) uses a simple regex to deny access to sensitive file patterns:
Blacklist:
- Name: Block .git/.svn access
- Match: URL Regex
- Pattern:
.(svn|htaccess|bash\_history|bash\_profile|git)
- Action: Deny
No whitelists are defined by default (you can add exceptions if needed).
How to Apply It
- Go to your SafeLine WAF management console.
- Create a new URL Regex Rule under your desired policy group.
- Paste the regex:
.(svn|htaccess|bash\_history|bash\_profile|git)
- Set action to Block/Deny.
- Deploy and test on a staging environment before production.
Best Practices
- Combine with other SafeLine rules: Pair this with User-Agent filtering and bot-blocking for full coverage.
- Keep sensitive files out of webroot: Blocking is good, but proper file placement is better.
- Regularly audit access logs: Ensure no unauthorized attempts are slipping through.
Join the SafeLine Community
If you continue to experience issues, feel free to contact SafeLine support for further assistance.



Top comments (1)
This is really helpful! Controlling access to Git and SVN repos is crucial to avoid leaks or accidental changes, and Safeline seems like a solid way to enforce that. For anyone interested in secure ways of sharing personal content and messages, you can visit theunsentproject.cc/ .