In today’s constantly evolving threat landscape, rate limiting has become a critical technique for protecting web applications from automated attacks—like bot scraping, brute-force logins, and denial-of-service attempts.
SafeLine WAF implements rate limiting with a strong focus on accuracy, performance, and flexibility.
In this post, we’ll walk through how SafeLine currently handles rate limiting—and how it’s evolving to meet more advanced challenges.
Current Approach: IP-Based Rate Monitoring
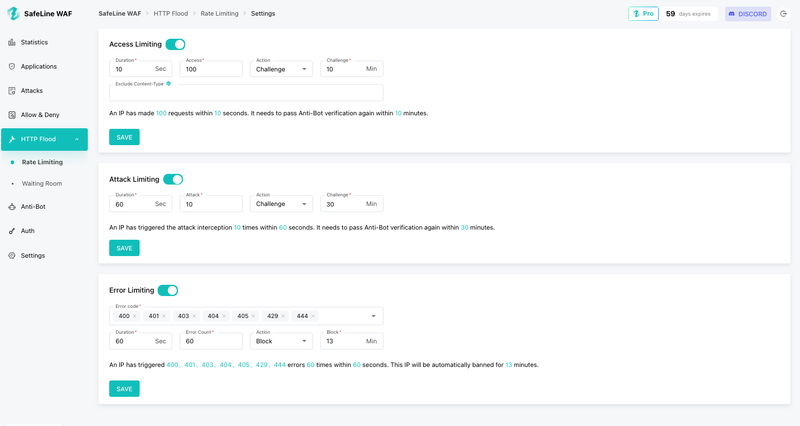
SafeLine’s current rate limiting system is based on per-IP request tracking. For each unique client IP, the system continuously monitors the number of incoming requests within a defined time window (usually per second).
When an IP exceeds the configured requests per second (RPS) threshold, SafeLine takes one or more of the following actions:
Enforcement Options
- Temporary blocking of the offending IP during a cooldown period.
- Progressive bot challenges, such as CAPTCHAs or JavaScript validation puzzles.
- Permanent blacklisting for persistent or clearly malicious IPs.
Real-World Example
Let’s say an attacker targets /api/login with a brute-force script to guess passwords. SafeLine detects the abnormal spike in login attempts from a single IP, blocks further requests, and protects your backend from abuse—all before the login logic is even triggered.
Why IP-Only Rate Limiting Isn't Enough
While IP-based protection works in many cases, it has known limitations—especially when facing:
- Botnets using rotating IPs
- Proxies or VPN abuse
- CDN-based anonymized traffic
To tackle this, SafeLine is building a more granular, context-aware rate limiting system.
What’s Coming: Fine-Grained, Smarter Rate Limiting
SafeLine’s next-gen rate limiting engine will support multiple dimensions for matching and control:
Context-Aware Policies
-
Per-endpoint rules: e.g., tighter limits on
/login,/signup,/checkout - User-Agent filtering: automatically lower thresholds for suspicious or bot-like headers
-
Custom logic based on:
- Headers
- Cookies
- Query parameters
- URI paths
This opens the door to route-specific and client-specific rate modeling, especially useful for modern applications with rich APIs.
Device Fingerprinting (Coming Soon)
To combat IP rotation and anonymization techniques, SafeLine is preparing to launch device fingerprinting as part of its rate limiting strategy.
How It Works:
- Identify clients based on browser behavior, TLS handshake, JS execution context, etc.
- Assign a fingerprint ID for each client, regardless of IP.
- Rate limiting and blocking decisions will then be tied to the fingerprint, not just IP.
This will dramatically reduce false negatives caused by rotating IPs, and make it harder for attackers to slip through the cracks.
Final Thoughts
SafeLine’s current IP-based rate limiting already provides strong protection against common automated threats. But the roadmap goes further—toward adaptive, intelligent rate limiting that understands behavior at a deeper level.
With features like endpoint-aware controls, custom match dimensions, and device fingerprinting on the horizon, SafeLine WAF is becoming one of the most effective defenses against modern bots and abuse patterns.
Feedback from users plays a huge role in shaping these capabilities.
If you have thoughts or feature requests, we’d love to hear from you.



Top comments (2)
Sheffield locksmith ensures quick and efficient solutions for all your lock and security needs, providing peace of mind across residential and commercial properties. In the digital realm, rate limiting in SafeLine WAF plays a vital role in protecting web applications from abuse and overload. By managing request traffic effectively, it enhances security and performance. As technologies evolve, future improvements promise even more adaptive and intelligent defenses—just like trusted locksmiths enhance real-world protection.
As more businesses plan for long-term stability whether in tech or personal finance adaptive safeguards are essential both for code and career planning. Just like SafeLine’s next‑gen rate limiting helps pension developers prepare for IP‑rotating botnets and future‑proof APIs, planning your financial future now ensures resilience down the line. For guidance on building retirement readiness and income planning.