Web Application Firewalls (WAFs) are essential for modern cybersecurity—but not all WAFs are built the same. Meet SafeLine, a powerful open-source WAF developed by Chaitin Tech.
If you're running a website or maintaining a cloud environment, this tool can be your first line of defense against SQL injections, XSS, DDoS, brute force, and aggressive crawlers.
Let’s dive into what makes SafeLine WAF stand out, how to deploy it, and what kind of real-world protection it provides.
🔍 What Is a WAF and Why You Need One
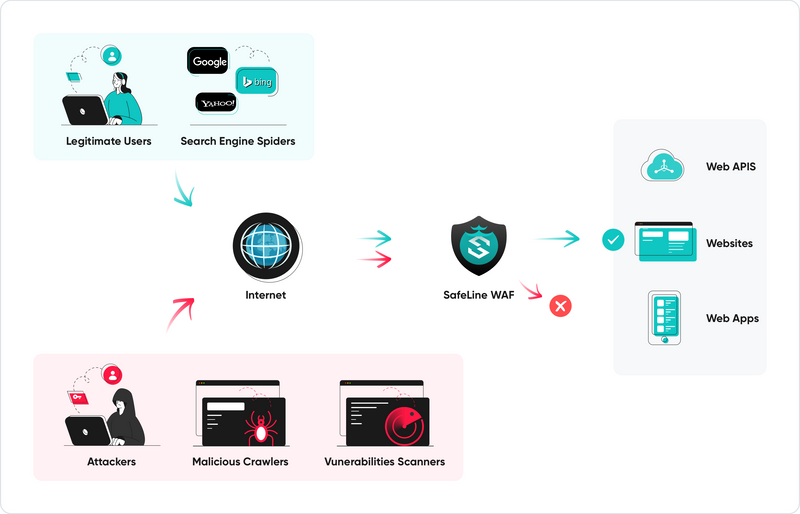
A WAF filters HTTP/HTTPS traffic to detect and block malicious behavior such as:
- SQL Injection
- XSS (Cross-site scripting)
- Path Traversal
- Command Injection
- Brute Force
- DDoS
- Web Crawlers
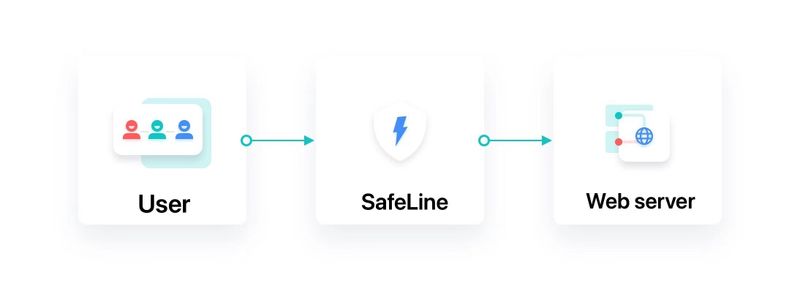
SafeLine sits between your users and your backend, analyzing requests in real time. It blocks attacks, logs attempts, and keeps your services online—even under stress.
🧠 Key Features of SafeLine WAF
✅ Blocks Common Web Attacks
SafeLine provides built-in protection against OWASP Top 10 vulnerabilities including SQLi, XSS, and XXE. It inspects HTTP requests in real time and stops malicious ones before they reach your app.
✅ Anti-DDoS and Rate Limiting
Automatically detects abnormal traffic and rate-limits suspicious IPs, stopping Layer 7 DDoS and HTTP flood.
✅ Bot and Crawler Defense
Human verification via CAPTCHA helps identify and block automated crawlers and scraping bots.
✅ Identity and Access Control
Supports fine-grained access policies, identity verification, and multi-factor auth to restrict access to sensitive endpoints.
✅ Dynamic Encryption
Protects frontend content using dynamic obfuscation techniques, making reverse engineering and exploit development harder for attackers.
✅ Cookie and CAPTCHA Validation
Generates unique cookies to prevent fake clients from bypassing security checks.
⚙️ Deployment Requirements
Before installing SafeLine, make sure your system meets the following:
- OS: Linux
- CPU Arch: x86_64 or ARM64 (SSSE3 required)
- Docker: 20.10.14+
- Docker Compose: 2.0.0+
- Minimum: 1 CPU core, 1 GB RAM, 5 GB disk
Minimum Server Requirements
To deploy SafeLine WAF, your server should meet the following minimum specifications:
- 1 CPU core
- 1 GB RAM
- 5 GB disk space
Before proceeding with the installation, it's important to verify that your server meets the system requirements. You can use the following commands to check your VPS environment:
uname -m
This command checks the CPU architecture of your server. If the output is x86_64, it means the server uses an x86_64 architecture; if it's aarch64, the architecture is arm64.
cat /proc/cpuinfo | grep "processor"
This command helps you view detailed CPU information, including the number of CPU cores. Knowing the number of cores gives you an idea of the server’s computing capability.
lscpu | grep ssse3
This command checks whether the CPU supports the SSSE3 instruction set. If ssse3 appears in the output, your CPU is compatible. If the result is empty, your CPU does not support SSSE3 and may not be able to run SafeLine properly.
🚀 Installation Guide
1. Install Docker
sudo apt-get update
sudo apt-get install -y apt-transport-https ca-certificates curl software-properties-common
curl -fsSL https://download.docker.com/linux/ubuntu/gpg | sudo apt-key add -
sudo add-apt-repository "deb [arch=amd64] https://download.docker.com/linux/ubuntu $(lsb_release -cs) stable"
sudo apt-get update
sudo apt-get install -y docker-ce docker-compose
2. Load SafeLine WAF Image
docker load -i image.tar.gz
3. Create docker-compose.yml
Configure environment variables and ports as needed.
4. Start WAF
docker-compose up -d
5. Configure Your Website in the Dashboard
- Add domains and port mappings
- Monitor traffic in real time
📊 Real-World Performance Testing
🛡️ OWASP Attack Simulation
# Example: Crawl attack test
for i in range(10000):
try:
requests.get(f"https://api.example.com/users/{i}", headers=random_headers())
except ChallengeBlocked:
blocked_count += 1
| Tool | Block Rate | CPU Load |
|---|---|---|
| Traditional WAF | 72% | 89% |
| SafeLine WAF | 96% | 43% |
📉 API Data Leakage Prevention
- No protection: 17MB/s data leak
- With dynamic token: 152KB/s
- With CAPTCHA: 9KB/s
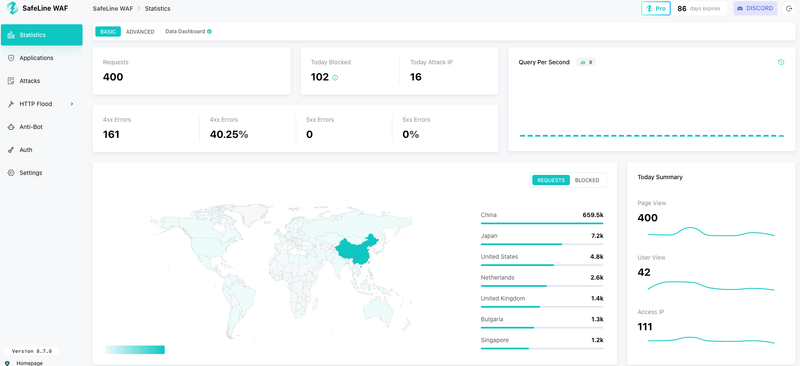
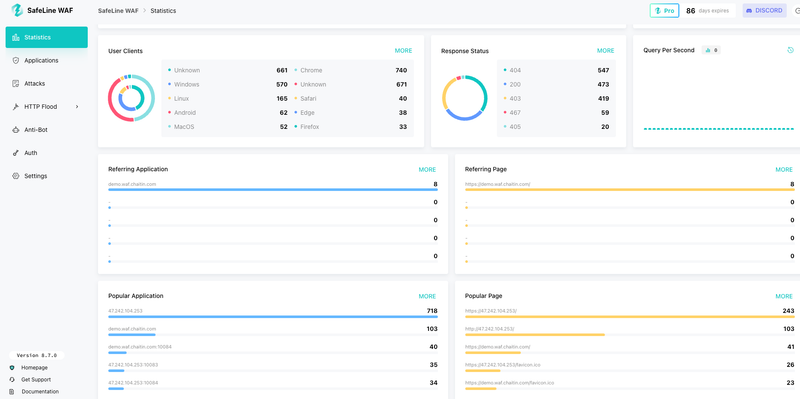
🔧 Daily Ops and Monitoring
- Live Traffic Logs
- Attack Reports with source IP, type, time
- Mitigation Suggestions for detected threats
- Custom Rules & Policies for SSL, headers, and access control
🧠 Why Choose SafeLine?
- Built by top-tier security researchers
- Lightweight yet powerful
- Free to use, open source
- Backed by Chaitin, the powerful team behind Blue Lotus CTF
💬 Want Help or a Full Config Template?
Join our community for real-time support and deployment templates. SafeLine is more than a tool—it's a growing ecosystem of defenders.
Let your backend rest. Let SafeLine do the fighting. 🛡️




Top comments (0)