WAF, short for Web Application Firewall, is a security layer that protects web applications by filtering and monitoring HTTP traffic. It’s specifically designed to prevent common web attacks such as SQL Injection and Cross-Site Scripting (XSS).
In general, WAFs come in three forms:
- Software WAFs (e.g., open-source or self-hosted)
- Hardware WAFs (appliances)
- Cloud WAFs (provided by CDN or security vendors)
In this article, we'll focus on deployment modes commonly used by hardware or appliance-based WAFs — and then introduce a free and modern WAF that’s easy to deploy.
Common WAF Deployment Modes
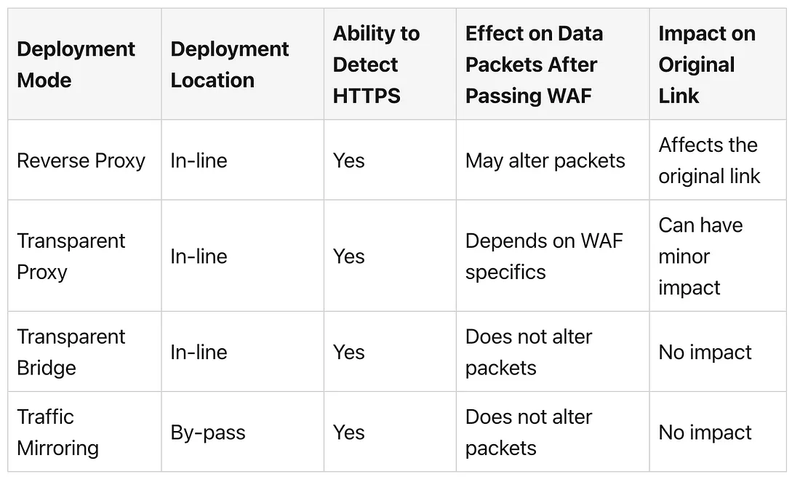
There are four main deployment modes for WAFs: Reverse Proxy, Transparent Proxy, Transparent Bridge, and Traffic Mirroring.
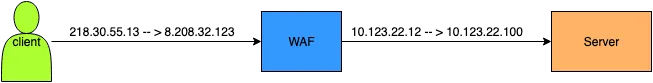
1. Reverse Proxy
A reverse proxy WAF acts as an intermediary between the client and the actual server. The client connects to the WAF, and the WAF forwards the request to the backend server. This makes the real server invisible to the client.
Client → WAF (Reverse Proxy) → Server
Advantages:
- The WAF has full control over HTTP(S) traffic.
- Easy to perform request/response inspection and rewriting.
- The real server's IP is hidden.
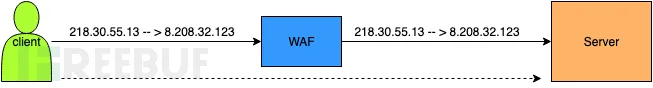
2. Transparent Proxy
A transparent proxy WAF intercepts traffic without modifying IP addresses. It typically sits inline between the client and server, making each side believe they are communicating directly.
Solid lines represent actual TCP connections, while dashed lines show perceived connections:
Client ———→ Transparent Proxy WAF ———→ Server
↖︎——————————————↗︎
(perceived connection)
Key features:
- No IP configuration changes required.
- Acts invisibly to both ends.
- Requires physical inline deployment (cable-level interception).
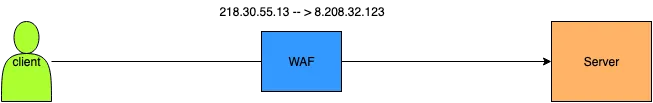
3. Transparent Bridge
Unlike transparent proxies, a transparent bridge WAF does not participate in the TCP handshake. It simply analyzes traffic without modifying or terminating connections.
It’s deployed inline just like a transparent proxy, but functions more like a passive observer.
Benefits:
- Truly “plug-and-play”: doesn’t interfere with TCP logic.
- Can be inserted or removed without interrupting traffic.
- More stable in case some traffic bypasses the WAF.
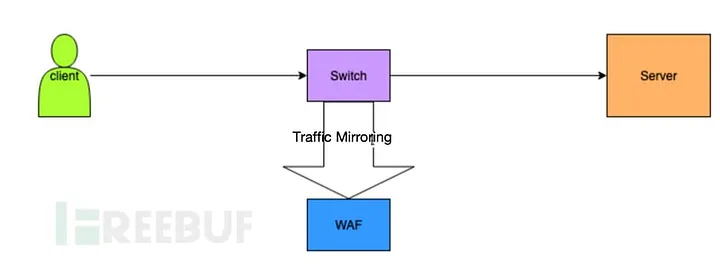
4. Traffic Mirroring
When inline deployment isn’t possible — for example, in production networks that can't be altered — traffic mirroring can be used.
In this mode, a switch copies HTTP(S) traffic and sends a mirrored stream to the WAF:
Client ↔ Switch ↔ Server
↘
WAF (receives mirrored traffic only)
The WAF inspects the mirrored traffic but does not interfere with the original communication.
Pros:
- Completely non-intrusive.
- Zero impact on production flow.
- Great for passive monitoring or alerting.
Comparison of Different Modes
A Free and Reliable WAF You Should Try: SafeLine
If you’re looking for a lightweight, open-source, and self-hosted WAF, I highly recommend trying SafeLine by Chaitin Tech.
SafeLine is:
- Free to use, with no feature limitations.
- Docker-deployable with one command.
- Capable of semantic analysis (far beyond regex filtering).
- Actively maintained and trusted by 300,000+ deployments.
You can deploy it on your own server and get full control over web traffic protection. It supports common WAF deployment modes (reverse proxy, transparent, mirroring, etc.), and has a clean web dashboard for rule management and log inspection.
👉 - GitHub Repository
👉 - Official Docs
👉- Discord Community
Whether you're building personal projects or managing production workloads, understanding WAF deployment modes — and having access to powerful free tools like SafeLine — is a great step toward modern web security.
Stay safe out there!



Top comments (4)
Door handles come in a variety of styles and materials, offering both functionality and aesthetic appeal for homes and offices. Choosing the right handle involves considering durability, design, and ease of use. From lever handles to knobs, modern options include finishes that resist wear and enhance interior decor. Proper installation ensures smooth operation and security. With the right selection and maintenance, door handles can provide long-lasting performance and elevate the overall look of any space.
Doncaster locksmith offers expert solutions for emergency lockouts, key replacements, and security upgrades with prompt and professional service. In the digital world, securing your systems is just as crucial. A WAF Deployment Guide paired with a free tool that works can safeguard web applications from threats and vulnerabilities. Whether you're protecting a property or a server, having the right tools and expertise ensures safety, reliability, and peace of mind in every environment.
Hey there! Thanks for breaking it down so clearly. This guide is super helpful, especially for beginners trying to understand WAF deployment.
I recently started working on a few client websites and was looking into reliable WAF options. SafeLine sounds like a solid choice! The fact that it’s free, open-source, and easy to deploy with Docker is a huge plus. Definitely going to give it a try.
Also, if you're not comfortable handling the technical side yourself or want a smoother setup, it’s always a good idea to hire developers who are experienced in web security and WAF integrations. They can help ensure everything’s configured properly from day one.
Appreciate the great info and recommendations. Safe coding!
Знаєте, іноді у повсякденній метушні ми забуваємо про такі прості, але важливі речі, як гігієна у ванній кімнаті. Особисто я нещодавно вирішив оновити душ і вибрав саме гігієнічний душ – це реально зручно та гігієнічно, особливо якщо у вас маленькі діти чи просто хочеться підтримувати чистоту на високому рівні. На сайті Гігієнічні душі можна знайти різні моделі, які легко монтуються та відмінно вписуються у будь-який інтер'єр. Раджу спробувати - якість води та комфорт використання відразу відчуваються, а догляд за ванною стає набагато простіше. Це дрібниця, але вона справді покращує повсякденне життя.