Cross-Site Scripting (XSS) is one of the most common and dangerous web security vulnerabilities. It allows attackers to inject malicious scripts into web pages viewed by other users — potentially stealing credentials, hijacking sessions, or performing other harmful actions in a user’s browser.
If you're building or maintaining a web app, understanding XSS is not optional. In this post, we’ll cover:
- What XSS is and how it works
- The main types of XSS attacks
- How to prevent XSS, with and without a WAF
- How modern WAFs like SafeLine help block XSS
What Is Cross-Site Scripting (XSS)?
XSS is a type of injection attack where the attacker sends malicious JavaScript that gets executed in the browser of other users. This typically happens when a web app takes user input and renders it in the HTML without proper sanitization.
Example (classic reflected XSS):
<!-- Unsafe: this echoes user input directly -->
<p>Hello, <?php echo $_GET['name']; ?></p>
If someone visits:
https://example.com/?name=<script>alert('XSS')</script>
The script runs in the victim’s browser — not what you want.
Common Types of XSS
1. Reflected XSS
- Payload is delivered via a URL or request parameter.
- Script executes immediately when the victim opens the malicious link.
- Common in search pages, error messages, etc.
2. Stored XSS
- The malicious script is saved on the server (e.g. in a comment or message).
- Every user who visits the page will run the script.
- More dangerous since it impacts multiple users over time.
3. DOM-Based XSS
- The vulnerability is in the frontend JavaScript code.
- The script reads from the DOM (e.g.
location.hash) and writes to the page without escaping. - No request sent to the server — purely a client-side issue.
How to Prevent XSS
Best Practices for Developers
- Escape output: Always escape user input before inserting it into HTML/JS.
- Use a framework: Modern frameworks like React, Vue, or Angular escape output by default.
- Validate input: Don’t trust any user input, even if it’s coming from a logged-in user.
- Use Content Security Policy (CSP): CSP can reduce the impact of XSS by blocking inline scripts.
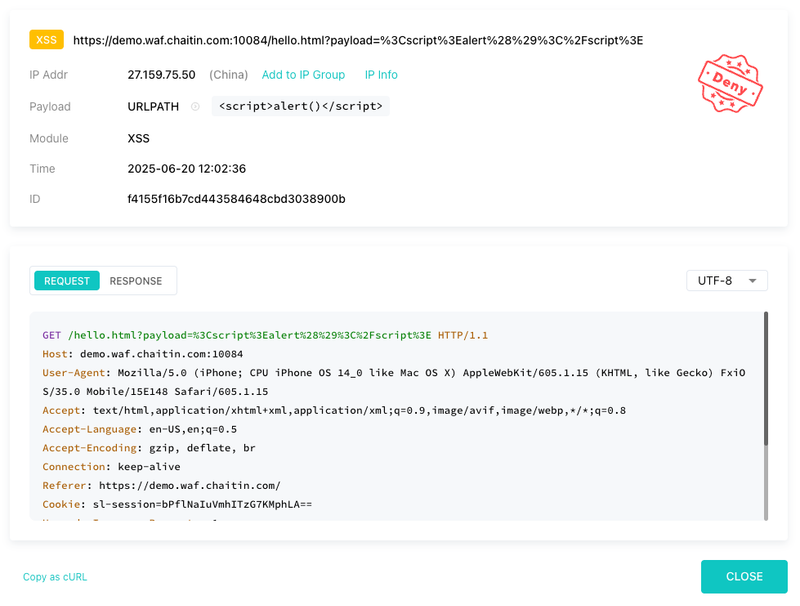
Using a WAF to Block XSS
Web Application Firewalls (WAFs) like SafeLine add an extra layer of protection:
- Detect suspicious patterns in requests (e.g.
<script>,onerror, JS functions). - Block known attack payloads automatically.
- Prevent both reflected and stored XSS, even if your backend code has flaws.
SafeLine uses semantic analysis, not just regex rules — meaning it’s better at catching obfuscated or encoded payloads.
Why XSS Still Matters in 2025
Despite being part of the OWASP Top 10 for years, XSS is still everywhere. With increasing use of client-side JavaScript, SPAs, and third-party scripts, the attack surface continues to grow.
If you're serious about security, protecting against XSS should be a priority.
Final Thoughts
XSS is dangerous, but it's preventable. By combining secure coding practices with the protection of a modern WAF like SafeLine, you can stop most XSS attacks before they reach users.



Top comments (1)
really?