When we were evaluating WAF options for our web app, the usual suspects—like Cloudflare—were on the shortlist. But ultimately, we went with SafeLine WAF from Chaitin Tech. Here’s why it's become our go‑to for robust, self‑hosted protection without the catch.
A WAF That Actually Fits Developers
SafeLine isn’t just another cloud vendor; it’s an open-source, self-hosted solution built with developers in mind. Want to inspect traffic, customize rules, or integrate with your CI/CD pipeline? You can. No black-box limitations.
Smart Detection > Rules-Based Mess
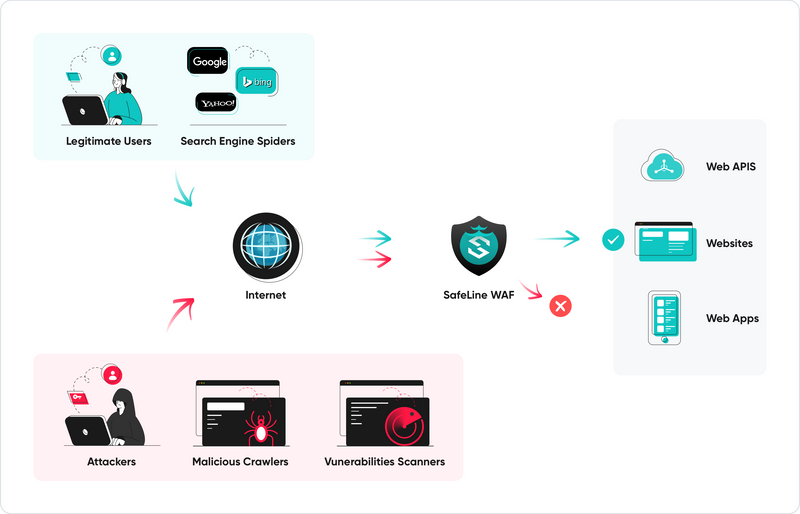
Thanks to intelligent semantic analysis and machine learning, SafeLine detects threats based on context—not just static patterns. It catches SQLi, XSS, SSRF, zero-days—even obfuscated payloads—while keeping false positives negligible (as low as 0.07%).
Layered Defenses That Matter
SafeLine comes with multiple built-in protection features:
- Web attack blocking: SQLi, command injection, path traversal, SSRF, XXE, etc.
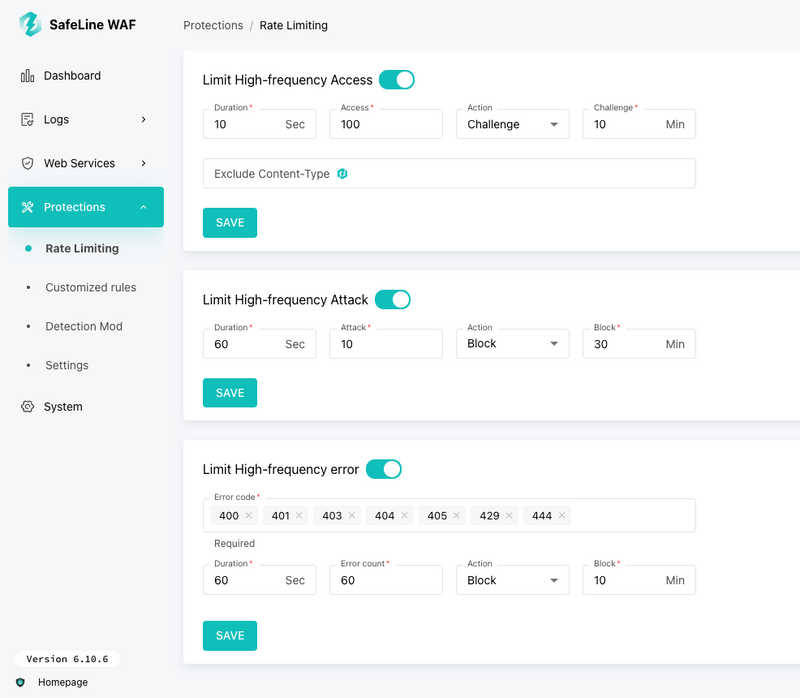
- Rate limiting & HTTP flood protection: Stop brute-force and DoS-style attacks.
- Bot protection: Dynamic challenges to block scrapers and malicious bots.
- Authentication challenges: Require GitHub/OIDC/password auth before access.
- Dynamic HTML/JS encryption: Obfuscate frontend code per request to evade scanners.
Architected for Scale & Control
SafeLine uses a modular architecture with microservices like tengine (proxy), detect (engine), mgt (admin panel), fvm (feature manager), and more. You can deploy via Docker, use the GUI for configuration, or automate everything via API.
It's DevOps-friendly and works well with Kong, Kubernetes, and cloud-native stacks.
Proven in Production
- 180,000+ deployments
- Over 1 million sites protected
- Processes more than 30 billion HTTP requests per day
- Detection accuracy ~99.45%, false positive rate ~0.07%
SafeLine vs Cloudflare: Quick Comparison
| Feature | Cloudflare (Free) | SafeLine WAF |
|---|---|---|
| Detection method | Rules-based | Semantic + ML |
| Self-hosted & private | ✖ | ✔ |
| Dynamic JS/HTML camo | ✖ | ✔ |
| Bot challenges | Paid only | ✔ |
| Rate limiting | ✔ | ✔ |
| Custom auth challenge | Limited | GitHub/OIDC built-in |
| False positives | Medium | Very low (~0.07%) |
Easy Setup, Full Control
Installation is quick with Docker. The admin GUI lets you view logs, manage rules, and monitor traffic. For power users, there's an API for scripting and automation. Whether you're protecting a monolith or microservices behind Kong, SafeLine integrates easily.
TL;DR
We chose SafeLine because:
- Open-source & self-hosted — Full control, no vendor lock-in.
- Advanced detection — Semantic analysis + ML means better coverage.
- Strong protection — Against bots, DDoS, bypasses, and unknown threats.
- Dev-friendly — Works with CI/CD, Docker, Kong, and modern infra.
- Battle-tested — Large-scale adoption, real-world effectiveness.
Join the SafeLine Community
SafeLine isn’t just a WAF—it’s a tool built for developers by security experts, letting you see, tune, and own your defense with precision. Try it out and shield your apps the right way.



Top comments (1)
We picked SafeLine over the usual WAF options because it gives developers full control without vendor lock-in. And just like how the SASSA status check lets users verify grant status directly, SafeLine lets you inspect, tune, and control everything, from traffic rules to threat detection, right from your own setup.
Some comments may only be visible to logged-in visitors. Sign in to view all comments.