Rate limiting is one of the most effective strategies for defending web applications against abusive behavior. Whether it's blocking DDoS attempts or taming aggressive bots, a good rate limiting strategy helps ensure your site stays fast, stable, and secure—even under pressure.
In this post, we’ll break down what rate limiting is, where it’s most useful, the pros and cons, and how SafeLine WAF makes it easy to implement.
Why Rate Limiting Matters
1. Block Malicious Traffic
Rate limiting helps identify and stop unusually high volumes of requests—often a sign of attacks like DDoS or CC (Challenge Collapsar) floods—before they bring down your site.
2. Save Bandwidth and Resources
By throttling request frequency, you can reduce strain on your backend services, lower bandwidth usage, and cut cloud or infrastructure costs.
3. Improve Stability and Availability
Spikes in traffic—whether malicious or not—can crash services. Rate limiting spreads out demand and keeps services online even under sudden load.
4. Enhance Threat Detection
When paired with behavioral analysis, rate limiting becomes a tool for spotting suspicious patterns and fine-tuning your security posture.
Common Downsides
1. False Positives for Legit Users
If rate limits are too aggressive, real users making legitimate repeated actions—like searching or refreshing—might get blocked.
2. Hard to Get the Threshold Right
Too loose? Attackers slip through. Too strict? Users get frustrated. Striking the right balance depends on your app’s specific usage patterns.
3. Monitoring Overhead
Rate limiting often requires real-time tracking of request data. At scale, this adds some overhead to servers and log storage.
Where to Apply Rate Limiting
Login Endpoints
Limit login attempts per IP to block brute-force attacks.
Search & Query Interfaces
APIs that trigger database queries are a popular abuse target. Throttle them to prevent abuse.
Public APIs
To avoid service degradation or API key abuse, rate limits are a must-have for open APIs.
File Downloads & Media Streaming
Protect your CDN and media endpoints from overuse by enforcing per-IP or per-user rate limits.
Common Rate Limiting Algorithms
Fixed Window
Allows a max number of requests per IP in a set time window (e.g. 5 requests per 10 seconds). Easy to implement, but can cause bursts near window reset times.
Sliding Window
Tracks request counts in a moving time window. More precise and better at smoothing out bursts than fixed window.
Leaky Bucket
Requests flow into a "bucket" and leak at a steady rate. Sudden spikes are automatically smoothed out, making this ideal for high-volume APIs.
Token Bucket
Tokens accumulate at a set rate and are consumed per request. Allows controlled bursts while still enforcing an overall limit.
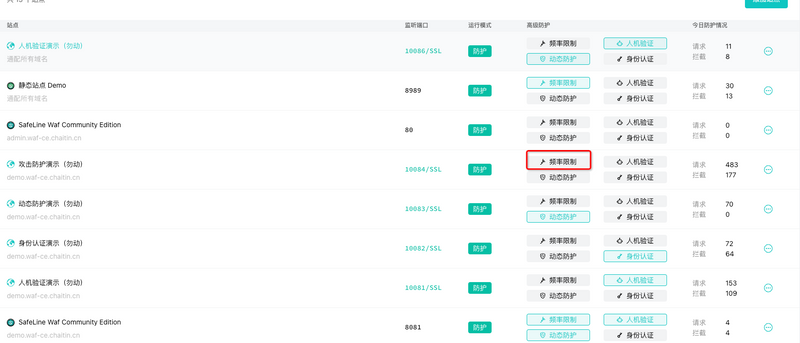
Rate Limiting with SafeLine WAF
SafeLine is an open-source Web Application Firewall that’s simple to deploy and powerful in real-world protection. One of its standout features is built-in, out-of-the-box rate limiting.
Once deployed, you can easily configure per-IP request thresholds. When an IP exceeds the defined rate, SafeLine automatically blocks further access—no extra setup needed.
Example Use Case:
- Limit login attempts to 10 per minute per IP
- Cap search requests to 100 per 5 minutes
- Throttle downloads to 20 files per hour per user
SafeLine’s flexible configuration lets you tailor protections based on endpoint type, HTTP method, or even URL pattern. Whether you're protecting an API or a content-heavy site, you get both control and convenience.
If you're running a public-facing web service, rate limiting isn’t optional—it’s essential. And with tools like SafeLine, you don’t need to be a security expert to implement it right.



Top comments (2)
Welcome to our Quran academy, where we offer the best online Quran classes to help you learn Quran online courses from the comfort of your home. Our Quran lessons online are designed to make learning easy and enjoyable for everyone.
This content not only informs jacksmith but also inspires, and I believe it will motivate others to explore the subject further and share their own experiences