SafeLine WAF is an open-source Web Application Firewall designed for developers who want powerful security without the steep learning curve. Built by security engineers with experience at top-tier tech companies (think BAT), SafeLine is designed to block threats like SQL injection, XSS, CSRF, and even bot attacks—right out of the box.
In this article, you’ll discover:
- What makes SafeLine different from traditional WAFs
- Why security engineers from top companies recommend it
- How you can deploy it quickly—for free
1. What Is SafeLine WAF?
SafeLine WAF was developed by Chaitin Tech over 9+ years with a simple mission: stop attackers before they even get close. It sits at the application layer and provides full-stack HTTP/HTTPS protection through semantic traffic analysis—rather than relying on static rules.
That means it can intelligently block:
- SQLi
- XSS
- CSRF
- Cookie tampering
- and more
All while keeping false positives impressively low—just 0.01% in production.
SafeLine also brings identity-aware protection. It supports MFA, OAuth 2.0, CAS, and WeChat OAuth, and integrates seamlessly with AD/LDAP systems for unified authentication and authorization.
2. Modern Identity and Access Management
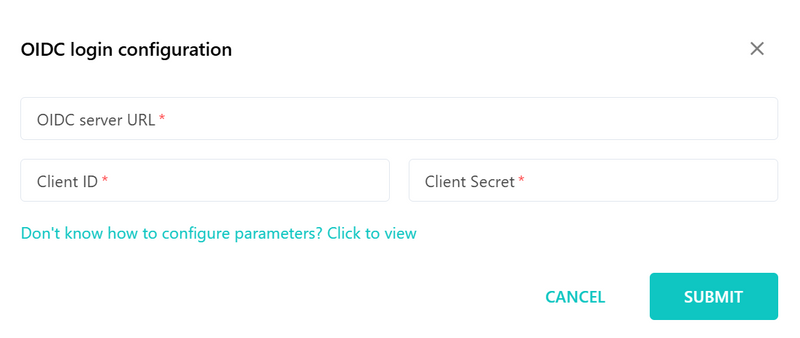
SafeLine’s built-in identity engine supports OIDC providers like Keycloak, Auth0, Okta, and Azure AD. This makes it easy to set up secure login flows across environments.
2.1 Multi-Factor, Multi-Layer Defense
- Customizable MFA: Combine passwords with OTPs or other dynamic tokens for sensitive operations.
- Anomaly Detection: Built-in UBA (User Behavior Analytics) detects abnormal login activity, like logins from distant locations in short timeframes.
- Bot-Proof Login Pages: Pages are encrypted, randomized, and even obfuscated with JS to block bots.
2.2 Unified Auth Across Platforms
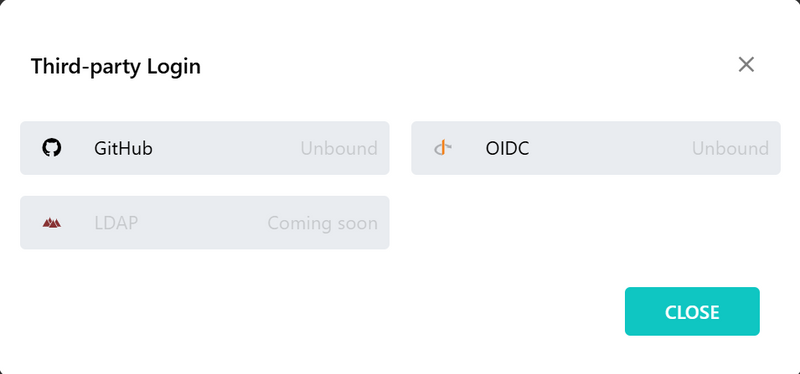
- Supports GitHub, OIDC, and more.
- GitHub OAuth login: ✅ under 2 seconds.
- RBAC lets you assign roles per user group. Ops teams manage configs; devs only see what they need.
3. Dynamic Defense: Make Static Pages Hard to Target
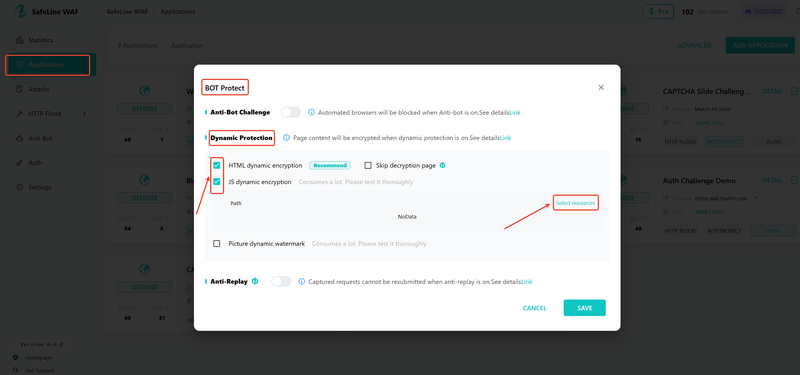
SafeLine goes beyond passive protection with dynamic obfuscation. When dynamic protection is enabled, it acts as a reverse proxy and actively rewrites your page code—HTML and JavaScript included—every time it’s served.
Why this matters:
- Frontend logic is hidden from scanners
- Bots and crawlers get blocked automatically
- Vulnerability scanners and automation tools fail
Each page load is unique. It’s like shifting sand under an attacker’s feet.
To enable:
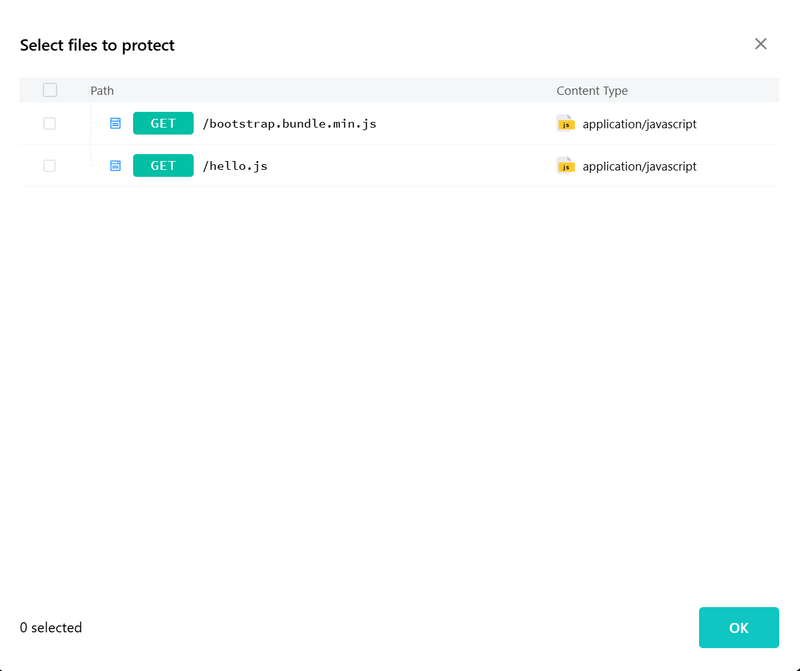
WAF → Applications → Bot Protect → Dynamic Protection → Toggle on HTML/JS encryption → Choose the pages to protect
4. Built to Scale, Designed to Be Simple
4.1 Flexible Deployment Options
- Docker & K8s Ready: Cloud-native support from day one.
- Reverse Proxy or Transparent Bridge: Choose what fits your stack.
- API Gateway Compatible: Works with Apache APISIX and others.
4.2 DevOps-Friendly Features
- One-Click Rule Sync: Sync 100+ policies across clusters in seconds.
- Visualized Threat Monitoring: Get a real-time view of active threats, attack types, and raw logs.
5. Why SafeLine Is Different
- Smarter Detection: Semantic parsing beats regex when it comes to detecting obfuscated payloads.
- Affordable: Community Edition is free. Pro version is just a fraction of the cost of traditional enterprise WAFs.
- Support: Dedicated 5×8 tech team to help you succeed.
SafeLine WAF isn’t just for researchers or hobbyists. It’s a real-world security platform made for developers, ops teams, and enterprises that care about fast deployment, deep visibility, and zero compromise.
Want to try it out or connect with other users?
👉 Join the SafeLine Discord
👉 Explore it on GitHub
Stay open source. Stay secure. SafeLine.





Top comments (1)
An open-source WAF supported by big-tech security pros is exactly what many devs need—a robust, transparent solution without vendor lock-in.
slope game