SafeLine now supports dynamic front-end protection — encrypting HTML and JavaScript responses in real time to stop automated attacks at the source.
What Is Dynamic Protection?
Dynamic Protection is a new web security technique that encrypts frontend assets — like HTML and JavaScript — on every request, turning static content into randomized, obfuscated code.
To human users, the page appears totally normal.
To crawlers, vulnerability scanners, or automation tools — it's a nightmare.
This protection is now supported in SafeLine WAF, and it’s highly effective against:
- Web scrapers
- Vulnerability scanners
- Exploit automation tools
- Brute-force credential stuffers
- Custom scripted bots
How It Works
When dynamic protection is enabled, SafeLine acts as a reverse proxy that rewrites HTML and JS responses dynamically, injecting encryption logic while keeping functionality intact.
Every user receives a slightly different version of the page, but the content renders exactly the same in the browser.
This breaks automation tools that depend on:
- Static DOM structure
- Repetitive responses
- Predictable HTML fields
- Payload reflection analysis
Real-World Examples
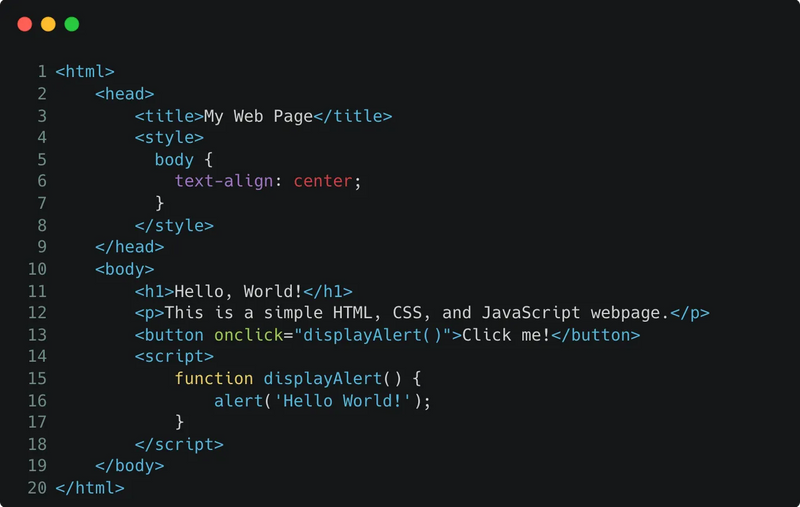
Before: Raw HTML
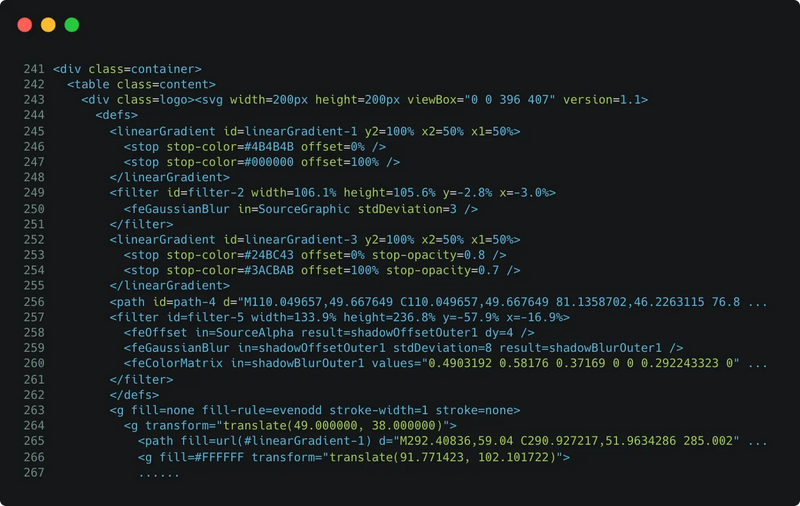
After: Encrypted HTML via SafeLine
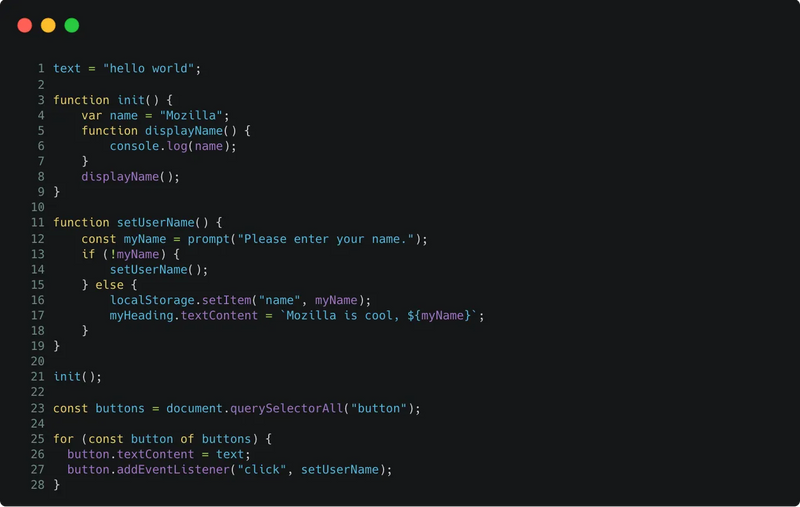
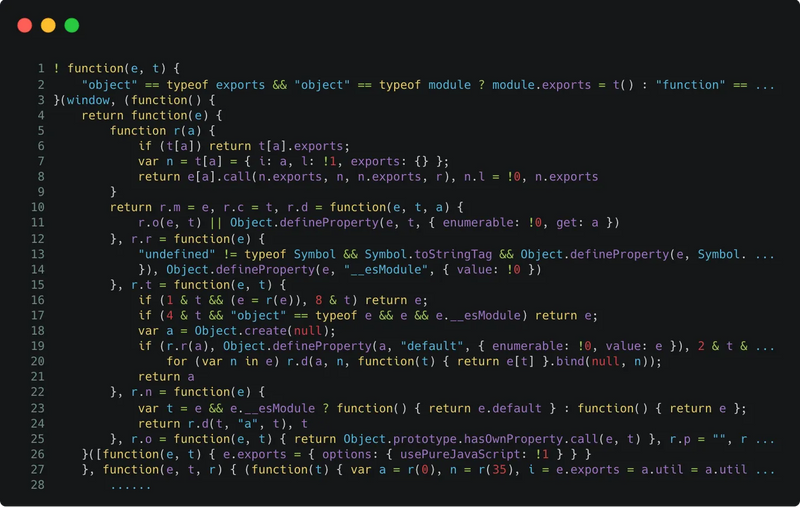
Before: JavaScript
After: Encrypted JavaScript via SafeLine
Every visit gets a different structure. Bots can't rely on static analysis anymore.
Breaking Crawlers and Scanners
Imagine a crawler trying to scrape structured data:
GET /info?id=666
Usually, it would:
- Request the page
- Parse the HTML
- Extract useful data
- Iterate on different IDs
But with dynamic protection:
- The page structure is encrypted and changes every time
- DOM parsing fails
- No consistent selectors
- Anti-crawling success
Now picture a vulnerability scanner:
- It checks SQLi by comparing
1=1vs1=2responses - It looks for payload reflections in response
- It analyzes error messages
- It brute-forces login forms
But with SafeLine’s dynamic defense:
- HTML/JS output changes on every request
- No reliable response comparison
- Scanner logic breaks entirely
- Automation fails silently
✨ Why It Matters
Most modern attacks — scraping, scanning, brute-force, vulnerability chaining — rely on consistent frontend structure. By breaking that assumption, SafeLine makes it extremely difficult for attackers to succeed without human interaction.
And best of all — this works transparently.
Users see the same content.
Browsers behave as expected.
Only bots suffer.
Try It Yourself
You can experiment with dynamic protection using SafeLine on GitHub. The project is open source and actively maintained by Chaitin Tech.
Final Thoughts
Dynamic protection is a game-changing concept for anti-automation defense. Rather than playing whack-a-mole with IP blocks or signatures, it flips the script — forcing bots to interpret a constantly shifting, encrypted frontend.
This is the kind of defense that turns automation into guesswork.
Join the SafeLine Community
If you continue to experience issues, feel free to contact SafeLine support for further assistance.



Top comments (0)